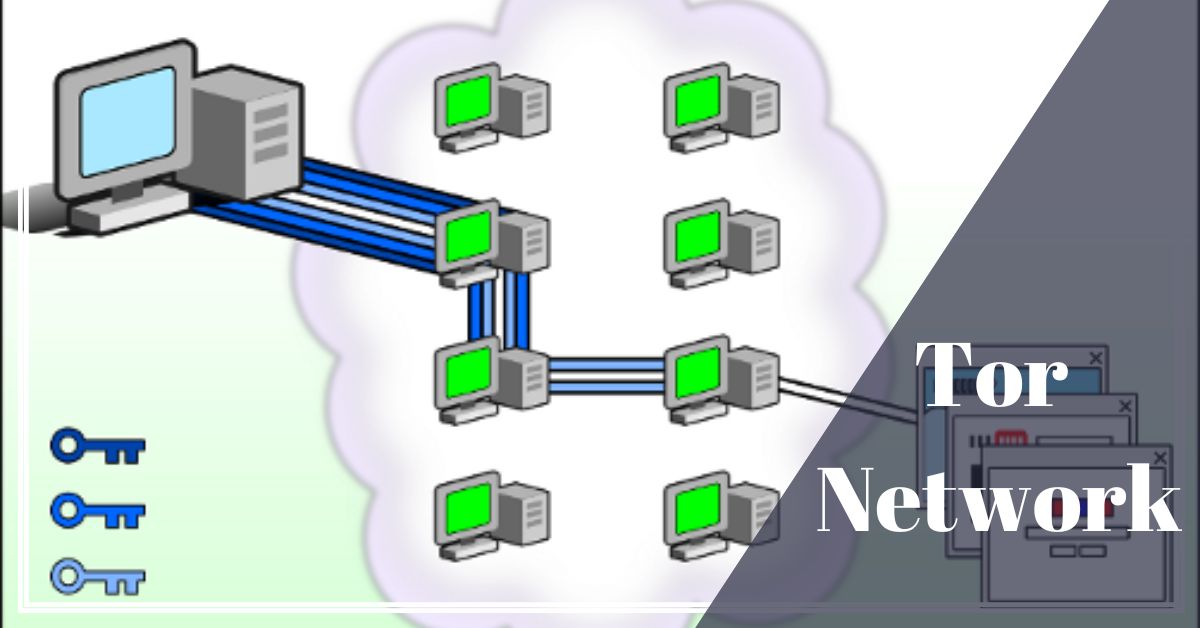
What is the Tor network? The Tor Network (simply Tor for short) aims to provide anonymous Internet browsing for all users. Tor uses the principle of onion routing to encrypt users’ connections and transfer data on the Internet. In this way, it allows anonymous, secure surfing on the Internet.
Contents
- What is the Tor network?
- How does Tor work?
- History of Tor
- Why is Tor Important
- Basics of Tor
- How Does Tor Ensure Anonymity?
- Benefits and Limitations of Using Tor
- Myths and Misconceptions About Tor
- Benefits and Limitations of Using Tor
- Myths and Misconceptions About Tor
- Tor and Darknet Markets
- Staying Safe While Using Tor
- Legal and Ethical Aspects of Tor Usage
- Tor in the News
- Frequently Asked Questions
- 1. Is Tor legal to use?
- 2. Can I access the regular internet while using Tor?
- 3. How does Tor protect my online privacy?
- 4. Are there any downsides to using Tor?
- 5. Is it true that Tor is only used by cybercriminals?
- 6. Can I use Tor on my mobile device?
- 7. Does Tor slow down internet speed?
- 8. What are some ethical considerations when using Tor?
- 9. Can government agencies trace Tor users?
- 10. Are there any risks associated with using Tor for online activities?
What is the Tor network?
The Tor Network, short for “The Onion Router,” is a privacy-focused network designed to provide anonymity and security for users browsing the internet. It accomplishes this by routing internet traffic through a series of volunteer-operated servers, known as nodes or relays, to obfuscate the origin and destination of data, making it difficult to trace back to the user.
How does Tor work?
Tor works by encrypting and routing internet traffic through a series of volunteer-operated relays.
- User Connection: When a user connects to the Tor network, their traffic is routed through a series of three types of nodes: Entry Nodes, Middle Nodes, and Exit Nodes.
- Entry Node: The user’s traffic is first sent to an Entry Node, which knows the user’s IP address but not the final destination of the traffic.
- Middle Nodes: From the Entry Node, the traffic is relayed through several Middle Nodes. Each Middle Node only knows the previous and next nodes in the chain but is unaware of the source and ultimate destination of the data.
- Exit Node: Finally, the traffic exits the Tor network through an Exit Node, which knows the destination of the data but doesn’t know the user’s IP address. This exit node then sends the user’s request to the target website or service.
- Encryption: Throughout this process, the data is encrypted in layers, similar to the layers of an onion (hence the name “The Onion Router”). Each node in the chain can only decrypt one layer, revealing the information necessary for routing but not the entire content.
- Anonymity: Because of this routing and encryption, it is extremely difficult for anyone, including ISPs, governments, or hackers, to trace the user’s activity back to their real IP address.
History of Tor
Origins of Tor
- Tor was initially developed by the United States Naval Research Laboratory in the mid-1990s as a means to protect government communications.
- It was later released as open-source software in 2002, making it available for public use.
Evolution and Growth
- The Tor Project, a non-profit organization, was established to maintain and improve the Tor network.
- Over the years, Tor has seen significant growth, with a global network of thousands of volunteer-run nodes.
- It has become a crucial tool for activists, journalists, whistleblowers, and individuals seeking online privacy.
Why is Tor Important
Anonymity and Privacy Online
- Tor is essential for protecting online privacy by preventing websites, governments, and ISPs from tracking and identifying users.
- It allows individuals to access the internet without revealing their location or identity, fostering freedom of speech and personal privacy.
Circumventing Censorship and Surveillance
- Tor helps users bypass internet censorship by allowing them to access blocked websites and services.
- It protects against surveillance, particularly in regions with oppressive governments that monitor internet activity.
- Tor plays a critical role in enabling free access to information and the exchange of ideas in restrictive environments.
Basics of Tor
The Tor Browser
- The Tor Browser is a web browser specifically designed to work with the Tor network.
- It’s based on Mozilla Firefox and configured to route all its traffic through the Tor network by default.
- The Tor Browser helps users access websites while maintaining their anonymity and privacy.
The Tor Network vs. VPNs
- The Tor network and VPNs (Virtual Private Networks) serve different purposes but can both enhance online privacy.
- Tor is primarily designed for anonymity and routing internet traffic through a series of nodes to obscure its origin.
- VPNs, on the other hand, create an encrypted tunnel between the user’s device and a VPN server, which can be located in various countries.
- While Tor is generally better for anonymity, VPNs are often faster and more suitable for general privacy and security needs.
How Does Tor Ensure Anonymity?
Onion Routing: The Core Concept
- The core concept behind Tor is onion routing, which involves multiple layers of encryption and routing through a network of nodes.
- Each node in the chain peels off one layer of encryption, revealing the routing information but not the source or destination.
- This process makes it incredibly difficult for anyone to trace the user’s traffic back to their IP address.
Encryption Layers in Tor
- Tor employs multiple layers of encryption, similar to the layers of an onion.
- When a user connects to the Tor network, their data is encrypted in layers, with each relay node in the chain adding its layer of encryption.
- The final layer is decrypted by the exit node, which forwards the traffic to its intended destination.
- This multi-layered encryption ensures that no single relay knows both the source and destination of the data, preserving anonymity.
Accessing the Tor Network
Downloading and Installing the Tor Browser:
- To access the Tor network, users can download the Tor Browser from the official Tor Project website.
- The Tor Browser is available for Windows, macOS, Linux, and Android.
- It’s designed for ease of use and comes preconfigured to work with the Tor network.
Configuring Tor for Enhanced Privacy
While the Tor Browser is already configured for privacy and anonymity, users can take additional steps to enhance their privacy:
- Use HTTPS: Ensure websites you visit use HTTPS for encrypted connections.
- Avoid Plugins: Disable or avoid using plugins like Adobe Flash, as they can compromise anonymity.
- Tweak Browser Settings: Adjust the browser’s security settings for your privacy preferences.
- Don’t Download Files: Downloading files through Tor can reveal your real IP address; avoid it when possible.
- Avoid Personal Information: Refrain from entering personal information on websites while using Tor.
Benefits and Limitations of Using Tor
Advantages of Using Tor
- Anonymity and Privacy: Tor provides a high degree of anonymity by concealing your IP address and routing your traffic through a series of relays, making it difficult for websites, governments, and hackers to trace your online activity back to you.
- Circumventing Censorship: Tor can help users in regions with internet censorship access blocked websites and services, promoting freedom of information and expression.
- Enhanced Security: While not primarily designed for security, Tor can add an extra layer of protection when using public Wi-Fi or in situations where you want to keep your online activities hidden.
- Protection from Traffic Analysis: Tor defends against traffic analysis, which means adversaries can’t easily determine what you’re doing online, even if they can’t identify you directly.
- Global Volunteer Network: Tor relies on a global network of volunteers running relays, which makes it difficult for any single entity to control or censor the network.
Drawbacks and Challenges
- Slow Connection Speeds: Tor can be significantly slower than regular browsing due to the routing of traffic through multiple relays, which can lead to frustration when streaming or downloading large files.
- Blocked Websites: Some websites may block access from Tor exit nodes, limiting your ability to use certain online services.
- Security Risks: While Tor provides anonymity, it doesn’t guarantee security. Users should be cautious about downloading files or sharing sensitive information over Tor, as malicious actors may operate exit nodes.
- Complexity: Tor can be challenging for inexperienced users to set up and configure properly. Using it incorrectly can reduce anonymity and privacy.
- Legal Implications: In some countries, using Tor may attract attention from authorities, leading to suspicion or legal repercussions. Users should be aware of their local laws and regulations.
Myths and Misconceptions About Tor
Common Misconceptions
- Tor is Only for Criminals: One of the most prevalent myths is that Tor is primarily used by criminals. While it can be used for illicit activities, it serves many legitimate purposes, including protecting the privacy and safety of activists, journalists, and whistleblowers.
- Tor is Completely Untraceable: Tor provides a high level of anonymity, but it’s not entirely untraceable. Determined adversaries with significant resources can potentially de-anonymize users.
- Tor is Always Slow: While Tor can be slower due to its routing through relays, the speed depends on various factors, including the number of relays, their bandwidth, and the user’s connection.
Debunking Tor Myths
- Tor is Legal: Using Tor is legal in most countries. It’s a tool that provides privacy and anonymity, and its legality depends on how it’s used.
- Not Just for Criminals: Tor is used by a diverse group of individuals, including activists, journalists, whistleblowers, and ordinary people concerned about online privacy. Legitimate use far outweighs malicious use.
- Regular Internet Use is Not Equivalent to Tor Use: Using Tor for regular browsing doesn’t make you suspicious. It’s a tool designed to protect your privacy, and many users utilize it for everyday activities.
Benefits and Limitations of Using Tor
Advantages of Using Tor
- Anonymity and Privacy: Tor provides a high level of online anonymity and privacy by concealing your IP address and routing your internet traffic through a series of volunteer-operated relays. This makes it challenging for websites and online entities to track your online activities back to your real identity.
- Circumventing Censorship: Tor can help users in regions with internet censorship access blocked websites and services. It allows individuals to bypass government-imposed restrictions on internet access, promoting freedom of information and expression.
- Protection from Surveillance: Tor safeguards against various forms of online surveillance, such as traffic analysis and eavesdropping. This is especially valuable for individuals who want to protect their online communications from prying eyes, including government agencies.
- Security in Public Wi-Fi: When using Tor, your data is encrypted between each relay, which can enhance security, especially when connected to public Wi-Fi networks where security risks are higher.
- Global Volunteer Network: Tor relies on a vast network of volunteer-operated relays worldwide. This decentralized structure makes it challenging for any single entity, including governments, to control or monitor the entire network.
Drawbacks and Challenges
- Slow Connection Speeds: The routing of internet traffic through multiple relays can significantly slow down your connection speed. This can be frustrating, particularly when streaming media or downloading large files.
- Blocked Websites: Some websites and online services block access from Tor exit nodes due to concerns about abuse. Users may encounter difficulties accessing certain websites or services.
- Security Risks: While Tor enhances anonymity, it does not guarantee complete security. Users must exercise caution, as malicious actors may operate rogue exit nodes to intercept or manipulate traffic.
- Complex Setup: Tor can be challenging for less tech-savvy individuals to set up and configure properly. Incorrect configurations or behaviors can potentially reduce anonymity and privacy.
- Legal Concerns: In some countries, using Tor may raise suspicions or draw attention from law enforcement agencies. It’s essential to be aware of the legal implications and regulations regarding Tor usage in your region.
Myths and Misconceptions About Tor
Common Misconceptions
- Tor is Only for Criminals: A widespread misconception is that Tor is primarily used by criminals for illegal activities. While it can be used for illicit purposes, it serves many legitimate and privacy-conscious users, including activists, journalists, and ordinary individuals.
- Complete Anonymity: Some people mistakenly believe that Tor provides absolute, unbreakable anonymity. While it offers a high level of anonymity, determined and well-funded adversaries can potentially de-anonymize users through sophisticated techniques.
- Slow All the Time: It’s a myth that Tor is slow all the time. Connection speed depends on various factors, including the number and bandwidth of the relays and the user’s own internet connection.
Debunking Tor Myths
- Legality: Tor is a legal and legitimate tool designed to protect online privacy. Its legality depends on how it’s used, and it is widely used for lawful and ethical purposes.
- Diverse User Base: Tor is used by a diverse range of individuals, including those concerned about online privacy, activists, journalists, researchers, and whistleblowers. Malicious use represents a minority of Tor’s user base.
- Balancing Privacy and Speed: Tor’s speed can vary, but it is not necessarily slow all the time. Users can find a balance between privacy and speed by configuring their settings and expectations appropriately.
Tor and Darknet Markets
Tor’s Association with the Darknet
- Tor has gained notoriety for its association with the Darknet, a part of the internet that is intentionally hidden and accessible only through Tor or other anonymizing tools.
- Darknet markets are online marketplaces on the Darknet that facilitate the sale of various goods, including illegal drugs, weapons, counterfeit items, and hacking services.
- While Tor is not inherently designed for illegal activities, its anonymity features have made it an attractive platform for those seeking to engage in illicit transactions.
Legal Implications and Ethical Considerations
- Using Tor itself is legal in most countries, as it is a privacy tool designed to protect online anonymity.
- However, engaging in illegal activities, even while using Tor, is illegal and can result in criminal charges.
- Ethical considerations come into play when individuals use Tor for illegal purposes, such as purchasing illegal substances or engaging in cybercrime.
- It’s important to remember that Tor serves many legitimate purposes, including protecting the privacy and safety of activists, journalists, and whistleblowers. The technology itself is neutral; it’s the actions of users that determine legality and ethics.
Staying Safe While Using Tor
Protecting Against Common Risks
- Use the Official Tor Browser: Download the Tor Browser from the official Tor Project website to ensure you’re using a trusted and secure version.
- Keep Software Updated: Regularly update the Tor Browser and your operating system to patch security vulnerabilities.
- Avoid Downloading Files: Downloading files through Tor can reveal your real IP address. Avoid downloading files unless absolutely necessary.
- Beware of Phishing: Be cautious when clicking on links or entering personal information, as Tor does not protect against phishing attacks. Verify the legitimacy of websites you visit.
- Use HTTPS: Ensure websites you visit use HTTPS for encrypted connections to protect against eavesdropping.
Safeguarding Personal Information
- Limit Personal Information: Refrain from sharing personal information, such as your real name, address, or phone number, while using Tor.
- Use Encrypted Services: Whenever possible, use services and websites that offer end-to-end encryption, as this enhances privacy.
- Consider a VPN (with caution): Some users opt to combine Tor with a VPN for added security. However, this should be done carefully, as it can introduce vulnerabilities if not configured correctly.
- Treat Tor as a Privacy Tool: Use Tor primarily for privacy and anonymity, not for illegal activities. Engaging in unlawful activities can have serious legal consequences.
- Be Mindful of Cookies: Cookies can be used to track your online activity. Configure your browser settings to reject third-party cookies.
- Use a Separate Identity: Tor allows you to create a new identity (get a new IP address) at any time. Use this feature to prevent websites from tracking your activities across sessions.
Legal and Ethical Aspects of Tor Usage
Legal Status and Regulations
- The use of Tor is generally legal in most countries. It’s a privacy tool developed to protect online anonymity, and its legality is similar to that of VPNs.
- However, the legality of specific actions conducted while using Tor, such as engaging in illegal activities, depends on local laws and regulations. Tor users are still subject to the laws of their respective jurisdictions.
Ethical Considerations of Tor
- Ethical considerations surrounding Tor usage primarily revolve around how it is used rather than the tool itself.
- Ethical use of Tor includes protecting one’s privacy, circumventing censorship for legitimate reasons (e.g., access to information and free expression), and using it for whistleblowing or journalism to expose wrongdoing.
- Unethical use of Tor includes engaging in illegal activities, harassment, or malicious behavior that harms others.
Tor in the News
Notable Tor-Related Events and Controversies
- Silk Road: The Silk Road, an infamous online marketplace for illegal goods, operated on the Darknet and made extensive use of Tor for anonymity. Its founder, Ross Ulbricht, was arrested and sentenced to life in prison in 2015.
- Operation Onymous: In 2014, law enforcement agencies from various countries collaborated to shut down several Darknet marketplaces, leading to arrests and the seizure of assets. This operation highlighted the challenges of maintaining anonymity on the Darknet.
- Exit Node Legal Issues: In some cases, operators of Tor exit nodes (the last nodes in the Tor network) have faced legal issues due to traffic passing through their nodes, potentially including illegal activities. This raises questions about liability and legal responsibility for Tor node operators.
- Ethical Debate: Tor has sparked ethical debates regarding whether it enables harmful activities. Advocates argue that the technology itself is neutral and serves vital purposes, while critics raise concerns about its misuse for illegal activities.
Alternatives to Tor
Other Privacy-Focused Tools and Networks:
- Virtual Private Networks (VPNs): VPNs encrypt internet traffic and provide some level of anonymity. They are generally faster than Tor but may not offer the same level of anonymity.
- I2P (Invisible Internet Project): Similar to Tor, I2P is an anonymous network that focuses on providing a secure and private communication platform.
- Freenet: Freenet is a decentralized, peer-to-peer network that emphasizes censorship resistance and anonymity. It is designed for secure and anonymous data storage and sharing.
- Subgraph OS: Subgraph OS is a privacy-focused operating system that includes security features and privacy enhancements for everyday computer use.
- Tails (The Amnesic Incognito Live System): Tails is a live operating system that can be booted from a USB drive. It is designed for privacy and leaves no trace on the host computer.
- Whonix: Whonix is a privacy-focused operating system that runs in a virtual machine and routes all traffic through Tor by default.
Frequently Asked Questions
1. Is Tor legal to use?
Yes, Tor is legal to use in most countries. It is a privacy tool designed to protect online anonymity. However, how you use Tor and the activities you engage in while using it must comply with local laws and regulations.
2. Can I access the regular internet while using Tor?
Yes, you can access the regular internet while using Tor. The Tor Browser allows you to visit websites on both the clearnet (regular internet) and the Darknet (hidden services accessible only via Tor).
3. How does Tor protect my online privacy?
Tor protects your online privacy by routing your internet traffic through a series of encrypted relays, making it difficult for websites and others to trace your online activities back to your real IP address. It also provides anonymity by concealing your identity.
4. Are there any downsides to using Tor?
Yes, there are downsides to using Tor, including slower internet speeds, potential incompatibility with some websites, and the risk of encountering malicious exit nodes. Additionally, some services may block or restrict access from Tor exit nodes.
5. Is it true that Tor is only used by cybercriminals?
No, Tor is not exclusively used by cybercriminals. While it has been associated with illicit activities on the Darknet, it serves many legitimate purposes, including protecting the privacy of activists, journalists, and individuals in need of online anonymity.
6. Can I use Tor on my mobile device?
Yes, you can use Tor on mobile devices. The Tor Project provides the Tor Browser for Android and iOS, allowing you to browse the internet anonymously on your smartphone or tablet.
7. Does Tor slow down internet speed?
Yes, using Tor can result in slower internet speeds due to the routing of traffic through multiple relays. The degree of slowdown depends on various factors, including the number and capacity of the relays and your own internet connection speed.
8. What are some ethical considerations when using Tor?
Ethical considerations include using Tor for legitimate privacy and security purposes, respecting the laws of your jurisdiction, and refraining from engaging in illegal activities while using the network. Responsible use of Tor is important to maintain its reputation as a privacy tool.
9. Can government agencies trace Tor users?
While Tor provides a high level of anonymity, determined and well-funded government agencies may have the capability to trace Tor users through advanced techniques. However, achieving this level of de-anonymization is exceptionally challenging.
10. Are there any risks associated with using Tor for online activities?
Yes, there are risks associated with Tor usage, including the potential for malicious exit nodes to intercept or manipulate traffic. Additionally, users must be cautious about sharing personal information, downloading files, or engaging in illegal activities while using Tor. Responsible and informed use of Tor is key to mitigating these risks.
In conclusion, Tor is a powerful tool for online privacy and anonymity, offering numerous benefits such as protection against surveillance, access to censored content, and safeguarding personal information. However, it’s important to use Tor responsibly and be aware of both its advantages and limitations.
Ultimately, Tor is a valuable tool for those who prioritize online privacy, but it should be used responsibly and in accordance with your region’s laws and ethical principles. By following best practices and staying informed, you can maximize the benefits of Tor while minimizing potential risks.

Information Security Asia is the go-to website for the latest cybersecurity and tech news in various sectors. Our expert writers provide insights and analysis that you can trust, so you can stay ahead of the curve and protect your business. Whether you are a small business, an enterprise or even a government agency, we have the latest updates and advice for all aspects of cybersecurity.