In today’s digital age, online security and user convenience are of paramount importance. As the number of online platforms and services continues to grow, the need for a secure and seamless authentication system becomes increasingly crucial. This is where OpenID comes into play.
In this article, we will dig deep into the world of OpenID, exploring its definition, working mechanism, benefits, and potential applications.
OpenID is a decentralized authentication system for web services. The identities of the authentication system are based on URLs and allow logging into multiple services with a single identity without re-entering username and password (single sign-on).
Contents
- What is OpenID?
- The Operating Principle of The ID Procedure
- How OpenID Works
- Benefits and Advantages of OpenID
- What Is OpenID Used for?
- How to Implement OpenID
- How to Enhance the Security in OpenID
- Common Myths about OpenID Debunked
- Frequently Asked Questions
- What is the main purpose of OpenID?
- Is OpenID the same as OAuth?
- Can I use OpenID with my existing accounts?
- How does OpenID enhance online security?
- Are there any privacy concerns with OpenID?
- Is OpenID suitable for small businesses?
- What are some notable examples of OpenID providers?
- Can I implement OpenID without technical expertise?
- Does OpenID work on mobile devices?
- How do I migrate my existing authentication system to OpenID?
What is OpenID?
OpenID is based on a decentralized concept and uses URL-based identities (IDs) for logging into web services. With the help of these identities, it is possible to log in to multiple services without having to re-enter a username and password. The concept thus supports single sign-on. The procedure’s prerequisite is a one-time registration with an ID provider and support by the desired service. It is an open specification from 2005 and version 2.0 was released in 2007.
Due to various limitations and missing features, the OpenID Foundation adopted a completely revised version of the protocol called OpenID Connect in 2014. To provide better support for mobile applications and more interoperability, the new version uses the so-called OAuth 2.0 framework.
The new protocol aims to create wider acceptance and more opportunities for single sign-on procedures on the network. The authentication mechanism of OAuth 2.0 differs significantly from that of OpenID.
History and development of OpenID
OpenID was first introduced in 2005 as an open standard for decentralized single sign-on authentication on the internet. It was created to address the challenges of managing multiple usernames and passwords across various websites and to provide a more user-friendly and secure authentication method.
OpenID’s development was led by Brad Fitzpatrick and championed by the OpenID Foundation. Over the years, it underwent several revisions and updates to improve security, usability, and interoperability.
Its evolution led to the creation of OpenID Connect, a more comprehensive identity protocol that combines OpenID with OAuth 2.0, providing enhanced features for authentication and authorization.
OpenID and OpenID Connect have played a significant role in shaping modern authentication practices and facilitating the growth of single sign-on solutions across the internet.
How OpenID differs from traditional username/password authentication
OpenID differs from traditional username/password authentication in several ways:
- Single Sign-On (SSO): OpenID allows users to authenticate themselves with a single set of credentials (their OpenID) across multiple websites and applications. This means users don’t need to remember separate usernames and passwords for each service, reducing the cognitive load and potentially enhancing security.
- Decentralized Authentication: In traditional authentication, each website/application maintains its own user credentials database. With OpenID, the authentication process is decentralized. Users have an OpenID that is managed by an identity provider (IDP), and this IDP vouches for the user’s identity to other websites. This reduces the need for websites to store sensitive user credentials.
- Privacy and Security: With traditional username/password authentication, websites have direct access to users’ passwords. In OpenID, the IDP handles the authentication process, and the user’s password is never shared with the websites they log into. This can enhance security and reduce the risk of password-related breaches.
- User Control: OpenID gives users more control over their personal information. Users can choose which attributes they share with websites through their OpenID, and they can update this information in one place (the IDP) rather than updating it separately on each website.
- Reduced Password Fatigue: Users often reuse passwords across multiple websites, which can be a security risk. OpenID reduces this risk by promoting the use of a single set of credentials managed by a trusted IDP.
- Authentication Flexibility: OpenID supports various authentication mechanisms beyond username/password, such as multi-factor authentication (MFA) and biometrics. This enables stronger authentication methods compared to the often-used username/password combination.
- Ease of Use: OpenID simplifies the login process for users. They can often log in with just a few clicks, as they don’t need to remember or enter a password for each website.
- Federated Identity: OpenID enables federated identity, where different organizations can use a common authentication system. This is useful for scenarios where multiple organizations collaborate and want to allow users from one organization to access resources in another without creating separate accounts.
- Open Standards: OpenID is built on open standards, making it easier for developers to integrate and implement. This promotes interoperability and reduces vendor lock-in.
The Operating Principle of The ID Procedure
To log in to web services, users need an ID. This can be issued by an ID provider. The decentralized architecture allows the existence of many different ID providers. The open standard ensures that the effort required to become a provider is relatively low. The ID has the format of a URL and could be, for example, username.example.com or example.com/username.
Web services can support both traditional username and password logon procedures and ID logon. If traditional logon procedures are not used, the effort required to securely manage usernames and passwords is eliminated. This effort is then shifted to the respective ID provider.
How OpenID Works
OpenID Providers (OPs)
OpenID Providers (OPs) play a crucial role in the authentication process of OpenID. They are responsible for verifying the user’s identity and providing the necessary authentication tokens to the Relying Parties (RPs), the websites or services the user tries to access. The OP acts as a trusted third party that vouches for the user’s identity.
Popular OpenID provider platforms include:
- Microsoft (Azure Active Directory)
- GitHub
- Auth0
- Okta
OpenID Consumers (RPs)
OpenID Consumers, also known as Relying Parties (RPs), are the websites or online services that want to authenticate users using OpenID. RPs rely on the authentication and identity information provided by the OP to verify the user’s identity. They are the ones who initiate the authentication process and receive the user’s identity information from the OP.
Integration of OpenID in various online services involves integrating the OpenID authentication flow into their login systems. This allows users to log in using their existing accounts with popular OpenID providers, reducing the need for users to create new accounts for every service they use.
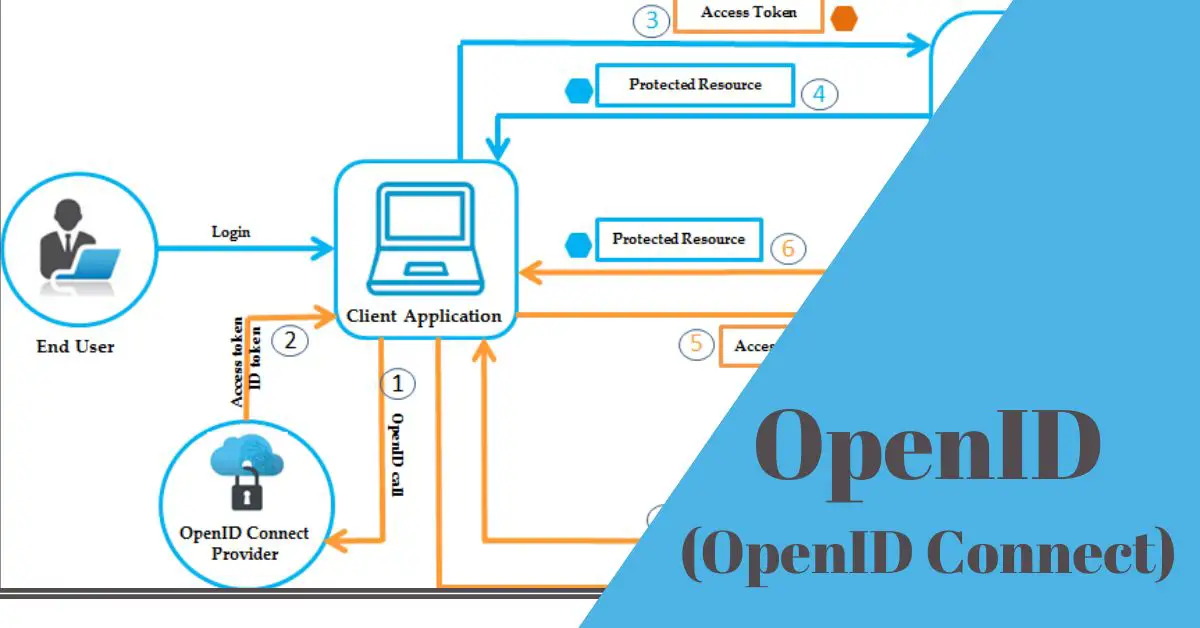
The Authentication Flow
The OpenID authentication flow involves several steps and interactions between the user, the OpenID Provider (OP), and the Relying Party (RP):
- User Initiation: The user attempts to log in to the Relying Party’s website or service using their OpenID identity.
- RP Request: The RP requests the user’s OpenID identity by redirecting the user to the OP’s authentication endpoint. This request contains information about the RP and the desired scope of access.
- User Authorization: The OP prompts the user to authenticate themselves and obtain their consent for sharing the requested identity information with the RP.
- Authentication and Consent: The user provides their credentials to the OP, which verifies their identity. The OP then asks the user to grant consent to share specific identity attributes with the RP.
- Authentication Token: Upon successful authentication and consent, the OP generates an authentication token (ID Token) containing the user’s identity information. This token is digitally signed by the OP to ensure its authenticity.
- Token Delivery to RP: The OP redirects the user back to the RP’s callback URL and ID Token.
- RP Verification: The RP receives the ID Token and verifies its authenticity by checking the digital signature and other security measures.
- User Access: Once the ID Token is verified, the RP grants the user access to their services, using the identity information provided in the token.
Throughout this flow, the user’s identity and credentials are handled by the OP, enhancing security and privacy for the user. The RP trusts the OP’s authentication process and identity verification, allowing for a seamless and secure authentication experience across various online services.
Benefits and Advantages of OpenID
OpenID offers a range of benefits and advantages that improve the user experience, enhance security, and provide convenience for both users and service providers.
Enhanced User Experience
- Streamlining User Logins (Single Sign-On – SSO): OpenID enables users to use a single set of credentials from their chosen OpenID provider to access multiple websites and services. This eliminates the need to remember and manage numerous usernames and passwords for different platforms, leading to a smoother and more efficient login process.
- Reducing Password Fatigue and User Friction: With OpenID, users don’t have to create and manage separate credentials for each service they use. This reduces the cognitive load associated with remembering multiple passwords, making the user experience more seamless and less frustrating.
Heightened Security Measures
- Enhanced Online Security: OpenID promotes better security practices by centralizing authentication with trusted identity providers. This means user credentials are stored and managed by a single, reliable source, reducing the risk of weak password practices or insecure storage by individual websites.
- Protection Against Phishing and Identity Theft: OpenID’s use of redirects and identity tokens can help mitigate phishing attacks. Users are redirected to their OpenID provider for authentication, reducing the chances of credentials being stolen through fraudulent websites. Additionally, the centralized nature of OpenID decreases the exposure of user credentials to potential attackers.
Cross-Platform Convenience
- Utilizing OpenID Across Different Websites and Services: OpenID allows users to use the same identity across multiple websites and services, promoting a consistent authentication experience. Users can log in with their familiar OpenID credentials, enhancing convenience and reducing the need to create new accounts.
- Achieving a Consistent Online Identity: OpenID enables users to establish a unified online identity that they can carry across various platforms. This can include profile information, preferences, and even verified attributes, creating a more personalized and coherent online presence.
What Is OpenID Used for?
With those advantages, OpenID is used widely in different areas.
Using OpenID login on the Internet
OpenID and variations of it have been implemented by many web services on the web. These include Yahoo, Google, Microsoft, PayPal, VeriSign and Facebook. According to the BSI, around 50,000 websites accepted the login procedure in 2009.
Due to its limitations, OpenID has been increasingly superseded by OpenID Connect and OAuth 2.0. Companies that support the more modern method include Deutsche Telekom, Microsoft, Google, IBM, Amazon. Salesforce.com and many more.
OpenID in E-Commerce: Simplifying Online Shopping
E-commerce platforms can leverage OpenID to simplify the shopping experience. Users can log in using their OpenID credentials, access their purchase history, and receive personalized recommendations, fostering customer loyalty.
OpenID in Social Media: A Unified User Experience
Social media platforms can adopt OpenID to enable users to sign in using their existing social accounts. This streamlines the registration process and encourages higher user engagement.
OpenID for Access Management in Enterprises
Enterprises can employ OpenID to manage employee access to various internal systems and applications securely. This centralized approach enhances data security and simplifies user provisioning and deprovisioning.
How to Implement OpenID
OpenID Connect vs. OAuth
OpenID Connect (OIDC): OpenID Connect is an identity layer built on top of OAuth 2.0. It provides user authentication and identity information in addition to the authorization capabilities of OAuth. OIDC is suitable when you want to not only authorize users to access resources but also obtain their identity attributes (such as name, email, and profile picture). It’s commonly used for single sign-on (SSO) scenarios.
OAuth 2.0: OAuth 2.0 is primarily an authorization framework that allows third-party applications to access a user’s resources (such as data or services) on their behalf without exposing the user’s credentials. OAuth is suitable when you need to delegate authorization to access resources but not necessarily authenticate the user directly.
Setting Up OpenID on Your Website
Here’s a step-by-step guide to integrating OpenID authentication into your website:
- Choose an OpenID Provider (OP): Decide which OpenID provider (Google, Facebook, Microsoft, etc.) you want to use for authentication.
- Register Your Application: Create an account with your chosen OpenID provider and register your application. You will receive client credentials (client ID and client secret) that your website will use to authenticate with the OP.
- Add Client-Side Code: Implement the OpenID Connect flow on your website’s front-end. This typically involves using libraries or SDKs provided by the OpenID provider to handle user authentication and obtain ID tokens.
- Implement Server-Side Code: On your server, verify the received ID token’s authenticity, validate its claims, and extract the user’s identity information. This step ensures the security and integrity of the authentication process.
- User Consent and Scopes: Request the necessary scopes to access the user’s identity attributes during authentication. Ensure you request only the required information and respect user privacy.
- Handle User Sessions: Once authenticated, establish a session for the user on your website. You might use cookies or other session management techniques.
- User Experience: Design a seamless user experience that guides users through the authentication process and handles any errors or exceptions gracefully.
Common Challenges and Solutions Related to OpenID Implementation
- Token Validation: Verifying the authenticity of ID tokens is crucial. Follow the OpenID provider’s documentation to correctly validate tokens using cryptographic methods.
- Redirect URLs: Ensure that your redirect URLs are correctly configured with your OpenID provider. Mismatched URLs can lead to authentication failures.
- Error Handling: Implement effective error handling to provide users with meaningful error messages and troubleshoot issues during the authentication process.
- Security Considerations: Follow best practices for securing sensitive information, including proper storage of client secrets and adherence to recommended security measures.
- User Experience: Prioritize a smooth user experience with clear instructions, well-designed interfaces, and user-friendly error messages.
How to Enhance the Security in OpenID
Enhancing security in OpenID implementation requires a focused approach. Here are the 7 most important things to prioritize:
- Token Validation and Verification: Thoroughly validate and verify the authenticity of tokens, such as ID tokens, received from the OpenID provider. Check digital signatures, token expiration, issuer information, and audience claims to prevent token-related vulnerabilities.
- Secure Communication: Implement strong encryption using protocols like HTTPS to ensure secure communication between users, your application, and the OpenID provider. This prevents data interception and tampering.
- Authorization Code Flow: Opt for the authorization code flow, especially for server-side applications. This flow ensures that tokens are exchanged on the server, reducing exposure in the browser and enhancing security.
- Strong User Authentication: Encourage or enforce strong user authentication methods, such as multi-factor authentication (MFA), to add an extra layer of security beyond the OpenID authentication process.
- Minimized Scope: Request and access only the necessary user attributes (scopes) required for your application’s functionality. Minimizing data access reduces the potential impact of a security breach.
- Secure Storage of Tokens: Store tokens securely, avoiding client-side storage for sensitive tokens. Implement appropriate encryption and protection mechanisms to safeguard tokens from unauthorized access.
- Regular Security Updates: Keep all components of your application, including libraries and dependencies, up to date. Promptly address security vulnerabilities by applying patches and updates.
Common Myths about OpenID Debunked
Let’s debunk some common myths about OpenID:
Myth 1: OpenID is the Same as OAuth.
Debunked: While related, OpenID and OAuth serve distinct purposes. OpenID Connect (OIDC) is built on top of OAuth 2.0 and provides both authentication and authorization, whereas OAuth primarily focuses on authorization for third-party access to resources.
Myth 2: OpenID is Insecure Due to Centralization.
Debunked: OpenID’s centralization of authentication with trusted identity providers enhances security by reducing the risk of weak password practices. It uses secure protocols and redirects to protect against phishing attacks.
Myth 3: OpenID Requires Sharing Full User Profile.
Debunked: OpenID allows users to control the attributes they share with each service, enhancing privacy. It offers fine-grained control over identity data, and only authorized scopes are shared.
Myth 4: OpenID is Only for Large Businesses.
Debunked: OpenID is suitable for businesses of all sizes. It simplifies authentication, enhances user experience, and can benefit small businesses by reducing friction and user management overhead.
Myth 5: OpenID is Complex to Implement.
Debunked: While OpenID implementation may require technical expertise, many OpenID providers offer libraries, SDKs, and comprehensive documentation to simplify integration. This makes implementation more accessible.
Myth 6: OpenID Sacrifices Privacy for Convenience.
Debunked: OpenID promotes user control over shared attributes. Users can choose what information to disclose, limiting data exposure. Proper implementation respects privacy while providing convenience.
Myth 7: OpenID is Phishing-Prone.
Debunked: OpenID’s use of redirects and token-based authentication helps prevent phishing attacks. Users are redirected to trusted identity providers, reducing the risk of credential theft through fraudulent websites.
Frequently Asked Questions
What is the main purpose of OpenID?
OpenID’s primary purpose is to simplify and enhance the user authentication process across multiple websites and services. It allows users to use a single set of credentials from their chosen OpenID provider to log in to various platforms. This streamlines user access, reduces the need to remember multiple usernames and passwords, and provides a more seamless and user-friendly online experience.
Is OpenID the same as OAuth?
While OpenID and OAuth are related, they serve different purposes. OpenID Connect (OIDC) is built on top of OAuth 2.0 and provides both authentication and authorization. OIDC adds identity information to the authorization process, allowing user attributes to be shared securely.
OAuth, on the other hand, is focused solely on authorization, allowing third-party applications to access a user’s resources without exposing their credentials.
Can I use OpenID with my existing accounts?
Yes, you can integrate OpenID authentication into your existing user account systems. Users with OpenID accounts with supported providers can use those accounts to log in to your service, reducing the need to create new accounts.
How does OpenID enhance online security?
OpenID enhances security by centralizing user authentication with trusted identity providers (IDPs). User credentials are stored and managed by the IDP, reducing the risk of weak password practices or data breaches. Additionally, OpenID’s use of redirects and cryptographic tokens helps protect against phishing attacks and unauthorized access.
Are there any privacy concerns with OpenID?
While OpenID enhances convenience, there can be privacy concerns if users are required to share more personal information than necessary. However, OpenID allows users to control the information they share with each service, and the use of trusted IDPs and secure token exchanges helps mitigate privacy risks.
Is OpenID suitable for small businesses?
Yes, OpenID can be beneficial for small businesses. It simplifies user authentication, reduces development effort, and provides a consistent user experience. OpenID also eliminates the need for users to create new accounts, potentially increasing user engagement.
What are some notable examples of OpenID providers?
Some well-known OpenID providers include Google, Facebook, Microsoft, GitHub, and LinkedIn. These platforms offer OpenID authentication services that you can integrate into your applications.
Can I implement OpenID without technical expertise?
While some technical expertise is generally required for implementation, there are libraries, SDKs, and guides provided by OpenID providers that can simplify the integration process. Working with a developer or using pre-built solutions can also help if you’re not a technical expert.
Does OpenID work on mobile devices?
Yes, OpenID can work on mobile devices. Most OpenID providers offer mobile-friendly authentication flows and provide SDKs for various mobile platforms, making it possible to implement OpenID-based authentication in mobile apps.
How do I migrate my existing authentication system to OpenID?
Migrating to OpenID involves integrating the OpenID authentication flow into your existing system. You’ll need to choose an OpenID provider, register your application, implement the necessary code changes, and ensure a smooth user experience during the transition. Proper planning and testing are essential for a successful migration.
OpenID stands as a beacon of innovation in the authentication realm. By merging security, convenience, and efficiency, it has the potential to reshape how we access online services. Embracing OpenID empowers both users and businesses, driving us towards a more interconnected and secure digital future.

Information Security Asia is the go-to website for the latest cybersecurity and tech news in various sectors. Our expert writers provide insights and analysis that you can trust, so you can stay ahead of the curve and protect your business. Whether you are a small business, an enterprise or even a government agency, we have the latest updates and advice for all aspects of cybersecurity.