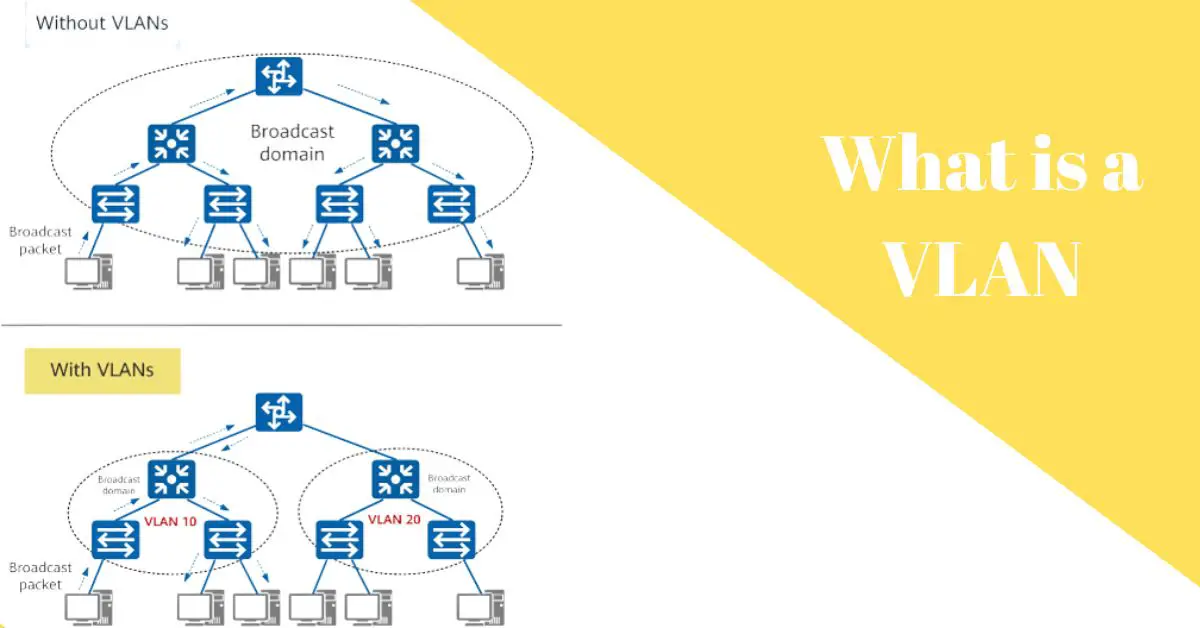
As computer networks continue to expand in size and complexity, new technologies are being developed to help manage and optimize data communication. One such technology is a VLAN, or Virtual Local Area Network.
VLANs allow devices to be grouped together into logical networks, even if they are physically located on different parts of a larger network. This can help to improve network efficiency, security, and manageability, among other benefits.
In this article, we’ll explore the ins and outs of VLANs, including what is VLAN, how they work, and the benefits they offer for modern network infrastructures.
Contents
- What is a VLAN?
- Reasons for using Virtual Local Area Networks
- How VLANs Work
- VLAN Tagging
- VLAN Membership
- VLAN Types
- VLAN Security
- VLANs vs Subnets
- Benefits of VLANs
- VLAN Best Practices
- Implementing VLANs in Your Network
- Common VLAN Problems and Solutions
- VLANs and Virtualization
- VLANs in the Cloud
- Vlan Trunking
- Vlan Configuration
- VLAN vs. LAN
- Future of VLANs
- FAQs about VLAN
What is a VLAN?
A VLAN is a logical subnetwork of a physical local area network (LAN). It divides the local network into logical segments, each forming its own broadcast domains. Virtual Local Area Networks can be implemented port-based or with the help of VLAN tags. VLAN technology is used, for example, to prioritize data traffic or to logically separate data streams.
VLAN is the acronym for Virtual Local Area Network. It is a logical subnetwork of a physical Local Area Networks (LANs). The Virtual Local Area Network forms a logical network segment and its own broadcast domain. VLANs can span multiple switches. They can be port-based or implemented using tagging.
The IEEE standard 802.1Q forms the technical basis for VLAN tagging. It works on the second layer of the OSI reference model and allows tagging information to be added to Ethernet frames. Tagging allows many logically separated VLANs to be transmitted simultaneously over a single network cable.
Typical applications of VLANs are the prioritization of data traffic or the logical separation of data streams.
Reasons for using Virtual Local Area Networks
Logical segmentation of physical local area networks using Virtual Local Area Networks is used for a variety of reasons. Typical reasons are:
- Logical separation of data streams
- Separation of productive environments and test environments
- Limitation of broadcast domains and reduction of broadcast traffic
- Separation of network segments for security reasons
- Separation of publicly accessible and internally accessible systems – Separation of public and private traffic
- Prioritization of data streams
- Separation of VoIP and data traffic
- Mapping of departmental structures independent of the location of the end devices.
How VLANs Work
A VLAN (Virtual Local Area Network) is a logical grouping of network devices that are connected to one or more physical LANs, but function as if they are on a single network segment. VLANs provide a way to divide a physical network into multiple virtual networks, which can improve network security, performance, and management.
When a VLAN is created, a unique VLAN ID is assigned to it, which is used to tag the network traffic associated with that VLAN. This tagging allows the network devices to differentiate between traffic belonging to different VLANs, even if they are on the same physical network.
To enable VLANs on a network, switches and routers are configured to support VLAN tagging. Switches are configured to assign VLAN IDs to the network ports that are connected to the devices. Routers are configured to route traffic between different VLANs, so that devices on different VLANs can communicate with each other.
VLAN tagging is implemented using two methods: port-based VLAN tagging and tag-based VLAN tagging.
In port-based VLAN tagging, each switch port is assigned to a specific VLAN. All traffic received on that port is tagged with the VLAN ID of the port and is forwarded to other ports that are also assigned to the same VLAN.
In tag-based VLAN tagging, a VLAN tag is added to each packet, which contains the VLAN ID. The VLAN tag is added to the packet header and is used to identify the VLAN that the packet belongs to.
VLANs can be used for a variety of purposes, such as isolating traffic between different departments within an organization, improving network performance by reducing broadcast traffic, and providing secure access to network resources.
VLAN Tagging
VLAN tagging is the process of adding a VLAN identifier or tag to a network frame so that the frame can be identified as belonging to a specific VLAN. The tag is added to the Ethernet frame header and is used to indicate which VLAN the frame belongs to. This allows network devices to differentiate between different VLANs and forward traffic appropriately.
There are two types of VLAN tagging: port-based and tag-based VLAN tagging.
In port-based VLAN tagging, each switch port is assigned to a specific VLAN. All traffic received on that port is tagged with the VLAN ID of the port and is forwarded to other ports that are also assigned to the same VLAN.
In tag-based VLAN tagging, a VLAN tag is added to each packet, which contains the VLAN ID. The VLAN tag is added to the packet header and is used to identify the VLAN that the packet belongs to. This allows the same physical port on a switch to carry traffic for multiple VLANs.
The most commonly used VLAN tagging protocol is IEEE 802.1Q, which is a standard for VLAN tagging in Ethernet networks. In 802.1Q, the VLAN tag is inserted into the Ethernet frame header between the source MAC address and the type/length field.
VLAN tagging is an important feature of VLANs because it enables network administrators to create multiple logical networks on a single physical network infrastructure. This allows for better network management, improved security, and more efficient use of network resources.
VLAN Membership
VLAN membership refers to the process of assigning network devices to specific VLANs. Devices can be assigned to a VLAN based on their physical location, network function, or user identity.
There are two ways to assign VLAN membership to a device: port-based VLAN membership and tag-based VLAN membership.
In port-based VLAN membership, each physical switch port is assigned to a specific VLAN. All traffic received on that port is assigned to the VLAN ID of the port and is forwarded to other ports that are also assigned to the same VLAN.
In tag-based VLAN membership, a VLAN tag is added to each packet, which contains the VLAN ID. The VLAN tag is added to the packet header and is used to identify the VLAN that the packet belongs to. This allows the same physical port on a switch to carry traffic for multiple VLANs.
Network administrators can use various methods to assign devices to VLANs. For example, devices can be assigned to VLANs based on their MAC address using a technique called MAC-based VLANs. In this method, the switch associates a specific VLAN ID with a specific MAC address. Any traffic received from that MAC address is assigned to the corresponding VLAN.
Another method is called port-based VLANs, where devices are assigned to VLANs based on which switch port they are connected to. This is useful in scenarios where devices are physically grouped together, such as in a particular building, floor, or department.
VLAN membership is an important aspect of VLANs because it enables network administrators to create multiple logical networks on a single physical network infrastructure. By assigning devices to different VLANs, administrators can improve network performance, security, and management.
VLAN Types
| VLAN Type | Description | Advantages | Disadvantages |
|---|---|---|---|
| Port-Based VLANs | Devices are assigned to VLANs based on which switch port they are connected to | Simple to set up and manage, ideal for grouping devices in physical locations such as floors or departments | Does not support devices that move to different physical locations |
| MAC-Based VLANs | Devices are assigned to VLANs based on their MAC address | Ideal for BYOD (bring your own device) scenarios where devices are owned by different people, provides flexibility | Requires manual configuration for each device’s MAC address |
| Protocol-Based VLANs | Devices are assigned to VLANs based on the protocol they are using, such as IP or IPX | Ideal for multi-protocol networks, provides flexibility | Not widely used as most networks now use IP |
| VLAN Trunking | Allows multiple VLANs to be carried over a single physical link between switches, using VLAN tags | Efficient use of network bandwidth, enables multiple VLANs to be carried over a single link | Requires VLAN trunking to be configured on all switches that the trunk passes through, which can be complex |
Port-Based VLANs
In port-based VLANs, devices are assigned to VLANs based on which switch port they are connected to. This method is simple to set up and manage, and is ideal for grouping devices in physical locations such as floors or departments. However, it does not support devices that move to different physical locations, as they would need to be manually reassigned to a different VLAN.
MAC-Based VLANs
In MAC-based VLANs, devices are assigned to VLANs based on their MAC address. This method is ideal for BYOD (bring your own device) scenarios where devices are owned by different people, as it provides flexibility. However, it requires manual configuration for each device’s MAC address, which can be time-consuming.
Protocol-Based VLANs
In protocol-based VLANs, devices are assigned to VLANs based on the protocol they are using, such as IP or IPX. This method is ideal for multi-protocol networks, as it provides flexibility. However, it is not widely used as most networks now use IP.
VLAN Trunking
VLAN trunking allows multiple VLANs to be carried over a single physical link between switches, using VLAN tags. This method is efficient in terms of network bandwidth, as it enables multiple VLANs to be carried over a single link. However, it requires VLAN trunking to be configured on all switches that the trunk passes through, which can be complex.
VLAN Security
VLANs can be used to improve network security by segmenting traffic and preventing unauthorized access to sensitive data. Here are some ways VLANs can be used to enhance network security:
- Isolation: By segregating network traffic into different VLANs, it is possible to isolate sensitive data and systems from the rest of the network. This prevents unauthorized access to critical resources and limits the impact of security breaches.
- Access Control: VLANs can be used to implement access control policies that restrict access to sensitive data and systems. Access control lists (ACLs) can be applied to VLANs to limit traffic to specific IP addresses or protocols.
- Broadcast Suppression: Broadcast traffic can be limited within VLANs, reducing the possibility of network congestion and preventing unauthorized access to data.
- VLAN Hopping Prevention: VLAN hopping is a security vulnerability where an attacker gains access to another VLAN by sending specially crafted packets. This can be prevented by implementing VLAN tagging and using VLAN trunks to ensure that traffic is only allowed on authorized VLANs.
- VLAN Monitoring: VLAN monitoring tools can be used to detect and alert administrators to any suspicious activity on the network. This includes traffic that violates access control policies, unusual traffic patterns, or unauthorized access attempts.
- VLAN Configuration Security: It is important to secure the configuration of VLANs themselves to prevent unauthorized changes or attacks. This can be achieved through the use of strong passwords, secure protocols, and regular monitoring of VLAN configuration changes.
VLANs can provide a powerful tool for enhancing network security by allowing network administrators to isolate and control access to critical resources. However, proper implementation and ongoing monitoring are essential to ensure that VLANs are effective in preventing security breaches.
VLANs vs Subnets
VLANs and subnets are two different network technologies that serve different purposes, but they can often be used together to achieve more efficient and secure networks.
A VLAN, or Virtual Local Area Network, is a logical network segmentation technique that allows a physical network to be divided into multiple virtual networks. VLANs are used to isolate traffic and provide better control over network resources. VLANs operate at Layer 2 of the OSI model, meaning they can only operate within a single broadcast domain.
A subnet, on the other hand, is a division of an IP network that allows a larger network to be split into smaller, more manageable sub-networks. Subnets are used to control network traffic, improve network performance, and provide security by isolating different groups of hosts from each other. Subnets operate at Layer 3 of the OSI model, meaning they can operate across multiple broadcast domains.
In general, VLANs are used to segregate traffic based on function or user group, while subnets are used to divide networks based on geographical location, function, or security requirements. VLANs can be used to separate traffic between different departments within a single building, while subnets can be used to separate traffic between different buildings or remote locations.
While VLANs and subnets serve different purposes, they can be used together to create more efficient and secure networks. For example, a network can be divided into multiple VLANs, with each VLAN containing multiple subnets. This allows for greater control over network resources, while also providing better security by isolating different groups of hosts from each other.
VLANs and subnets are two different network technologies that serve different purposes, but they can often be used together to create more efficient and secure networks. VLANs are used to isolate traffic and provide better control over network resources within a single broadcast domain, while subnets are used to control network traffic, improve network performance, and provide security across multiple broadcast domains.
Benefits of VLANs
There are several benefits of using VLANs in a network:
- Security: VLANs provide enhanced security by isolating traffic between different user groups or functions. This can prevent unauthorized access to sensitive data and limit the impact of security breaches.
- Traffic Control: VLANs allow network administrators to control traffic flow and optimize network performance. By segregating traffic based on user groups or functions, bandwidth can be allocated more efficiently and network congestion can be reduced.
- Cost Savings: VLANs can help reduce network costs by eliminating the need for physical network segmentation. Instead of using separate physical networks for different groups of users, VLANs allow multiple virtual networks to operate on a single physical network.
- Flexibility: VLANs provide greater flexibility in network design and allow for easier network reconfiguration. By separating logical networks from physical networks, network administrators can change network configurations without having to physically rewire the network.
- Simplified Network Management: VLANs allow for easier network management by providing logical segmentation of the network. This can simplify network troubleshooting, reduce the risk of network outages, and provide greater visibility into network traffic.
- Improved Collaboration: VLANs can improve collaboration by allowing different user groups or departments to communicate more efficiently. By providing a dedicated network for specific groups, VLANs can help streamline communication and improve productivity.
VLANs provide several benefits for network design and management, including enhanced security, traffic control, cost savings, flexibility, simplified network management, and improved collaboration. By using VLANs, network administrators can design and manage networks more efficiently and effectively.
VLAN Best Practices
Some best practices for implementing VLANs in a network:
- Plan the VLAN Architecture: Before implementing VLANs, it’s important to plan the VLAN architecture based on the needs of the organization. This includes determining which groups of users or functions require network isolation, and how many VLANs are needed to support the network.
- Use Standard Naming Conventions: It’s important to use standard naming conventions for VLANs to ensure consistency and ease of management. For example, VLAN names can be based on the function or location of the network, or can use numerical designations.
- Limit the Number of VLANs: While VLANs can provide network segmentation and improve network performance, too many VLANs can make the network more complex and difficult to manage. It’s important to limit the number of VLANs to a manageable number based on the needs of the organization.
- Implement VLAN Tagging: VLAN tagging is essential for ensuring that network traffic is routed to the correct VLAN. It’s important to ensure that all devices on the network support VLAN tagging and are configured correctly to ensure traffic is properly routed.
- Implement VLAN Access Control: VLANs should be configured with access control policies to ensure that only authorized users can access the network. This can include using access control lists (ACLs) to restrict access to specific IP addresses or protocols.
- Regularly Monitor VLANs: It’s important to regularly monitor VLANs to ensure that they are functioning properly and that there are no security vulnerabilities. This can include monitoring VLAN traffic, detecting unauthorized access attempts, and ensuring that VLAN configurations are secure.
- Use VLAN Trunking: VLAN trunking allows multiple VLANs to be carried over a single network connection, reducing the need for multiple physical connections. It’s important to use VLAN trunking to improve network efficiency and reduce costs.
Implementing VLANs requires careful planning, configuration, and monitoring to ensure that they provide the desired network segmentation, security, and performance benefits. By following these best practices, network administrators can design and manage VLANs more effectively and efficiently.
Implementing VLANs in Your Network
Implementing VLANs in your network involves several steps, including:
- Identify VLAN Requirements: Before implementing VLANs, identify the user groups or functions that require network isolation. Determine the number of VLANs needed to support the network, and decide on naming conventions for VLANs.
- Configure VLANs: Configure VLANs on your network devices, such as switches and routers. This involves assigning VLAN IDs, configuring VLAN tagging, and configuring VLAN access control policies.
- Assign VLANs to Network Devices: Assign VLANs to network devices, such as servers, printers, and user devices. This ensures that network traffic is properly routed to the correct VLAN.
- Configure VLAN Trunking: If you have multiple switches, configure VLAN trunking to allow multiple VLANs to be carried over a single network connection.
- Test VLANs: Test VLANs to ensure that they are functioning properly and that traffic is being routed correctly. This includes verifying VLAN configurations, testing VLAN traffic, and checking access control policies.
- Monitor and Manage VLANs: Monitor VLANs to ensure that they are functioning properly and that there are no security vulnerabilities. This includes monitoring VLAN traffic, detecting unauthorized access attempts, and ensuring that VLAN configurations are secure.
Overall, implementing VLANs requires careful planning, configuration, and monitoring to ensure that they provide the desired network segmentation, security, and performance benefits. By following these steps, network administrators can design and implement VLANs more effectively and efficiently.
Common VLAN Problems and Solutions
Some common VLAN problems that can arise in a network, along with their solutions:
- VLAN Misconfiguration: VLAN misconfiguration can cause network connectivity issues and security vulnerabilities. The solution is to ensure that VLANs are configured correctly and that VLAN IDs and access control policies are properly assigned.
- VLAN Trunking Issues: VLAN trunking can sometimes cause issues such as misconfigured trunk ports or incorrect VLAN tagging. The solution is to ensure that trunk ports are configured correctly and that VLAN tagging is properly configured.
- VLAN Access Control Problems: Access control problems can occur if VLAN access control policies are not properly configured or if there are unauthorized users on the network. The solution is to configure access control policies correctly and to monitor network traffic for unauthorized access attempts.
- VLAN Security Vulnerabilities: VLANs can be vulnerable to security threats such as VLAN hopping, where attackers can gain access to other VLANs on the network. The solution is to use VLAN access control policies and VLAN isolation to prevent unauthorized access.
- VLAN Performance Issues: VLAN performance issues can occur if VLANs are configured incorrectly or if there is too much network traffic. The solution is to ensure that VLAN configurations are optimized for performance and to monitor network traffic to identify performance issues.
- VLAN Design Issues: VLAN design issues can occur if the network is not properly designed to support VLANs, such as if there are too many VLANs or if VLANs are not properly segmented. The solution is to plan VLAN architecture carefully and to ensure that VLANs are properly segmented and optimized for network performance.
By following best practices for VLAN implementation, monitoring, and management, many common VLAN problems can be prevented or quickly resolved. Regular monitoring and maintenance of VLANs is important to ensure that they continue to provide the desired network segmentation, security, and performance benefits.
VLANs and Virtualization
VLANs and virtualization are closely related because both technologies are used to segment and manage network resources more efficiently.
In virtualized environments, such as virtualized servers or cloud computing environments, VLANs are often used to provide network segmentation for virtual machines (VMs). Each VM can be assigned to a specific VLAN, allowing them to communicate only with other VMs in the same VLAN. This provides increased security and performance by reducing network traffic and limiting access between different virtual environments.
VLANs can also be used to provide network connectivity for virtual switches, which are used to connect VMs to physical network resources. By using VLAN tagging, virtual switches can identify and route traffic between different VLANs, providing network segmentation and isolation for virtualized environments.
In addition to providing network segmentation, VLANs can also be used to optimize network performance in virtualized environments. By configuring VLANs to support Quality of Service (QoS) policies, network administrators can prioritize network traffic for different virtualized applications or services based on their importance or bandwidth requirements.
VLANs and virtualization are complementary technologies that can be used together to improve network performance, security, and manageability in virtualized environments. By properly configuring and managing VLANs in virtualized environments, network administrators can optimize network resources and ensure that virtualized applications and services are properly secured and isolated.
VLANs in the Cloud
VLANs can be used in cloud environments to provide network segmentation and isolation for virtualized resources such as virtual machines, containers, and network functions. This can be done by using VLAN tagging on virtual network interfaces to identify and route traffic between different VLANs in the cloud environment.
In cloud environments such as Amazon Web Services (AWS) and Microsoft Azure, VLANs are often used to provide network segmentation for virtual private clouds (VPCs). VPCs allow customers to create isolated network environments within the cloud provider’s infrastructure, using VLAN tagging to ensure that traffic is properly routed and isolated.
In addition to providing network segmentation, VLANs can also be used to improve network performance in cloud environments. By configuring VLANs to support Quality of Service (QoS) policies, network administrators can prioritize network traffic for different cloud applications or services based on their importance or bandwidth requirements.
However, when implementing VLANs in the cloud, network administrators should be aware of potential security risks. VLAN hopping attacks, for example, can exploit misconfigured VLANs to gain unauthorized access to other VLANs in the same network. To mitigate this risk, cloud providers often provide security controls such as virtual firewalls and access control policies to restrict access to VLANs and VPCs.
VLANs can be a useful tool for providing network segmentation and improving network performance in cloud environments. However, it is important to properly configure and manage VLANs to ensure that they do not create security vulnerabilities or other network issues.
Vlan Trunking
VLAN trunking is a technology that allows multiple VLANs to be carried over a single physical link between network switches. Trunking is commonly used in larger networks that require the segregation of traffic for security or organizational reasons.
In a trunking scenario, the switch port that connects to another switch or a router is designated as a “trunk port.” This port will carry traffic for multiple VLANs, with each VLAN being identified by a unique VLAN ID. The traffic is encapsulated with a VLAN tag that includes the VLAN ID, which allows the receiving switch or router to differentiate between the different VLANs.
One of the primary benefits of VLAN trunking is that it allows network administrators to more efficiently use their network resources. Instead of requiring a separate physical link for each VLAN, multiple VLANs can be carried over a single link. Additionally, trunking can reduce the amount of wiring required, simplify network management, and provide greater flexibility in how network traffic is routed.
To configure VLAN trunking, network administrators must ensure that both switches support trunking and that the trunking protocol is properly configured. There are several trunking protocols available, including Cisco’s proprietary Inter-Switch Link (ISL) protocol and the industry-standard IEEE 802.1Q protocol.
VLAN trunking is a useful technology for organizations that require the segregation of traffic for security or organizational reasons. By allowing multiple VLANs to be carried over a single physical link, VLAN trunking can reduce costs, simplify network management, and provide greater flexibility in how network traffic is routed.
Vlan Configuration
Configuring VLANs involves several steps, including creating VLANs, assigning ports to VLANs, and configuring VLAN trunking. The following are the basic steps for VLAN configuration:
- Create VLANs: The first step is to create the VLANs you need. VLANs can be created using the switch’s configuration interface, either via the command line or a graphical user interface (GUI). VLANs are identified by a unique VLAN ID, which ranges from 1 to 4094, although not all VLAN IDs are available for use.
- Assign Ports to VLANs: After creating the VLANs, you need to assign switch ports to the appropriate VLANs. Ports can be assigned to a VLAN using the switch’s configuration interface, either by specifying individual ports or by using range commands to assign multiple ports to a VLAN at once.
- Configure VLAN Trunking: If you need to carry multiple VLANs over a single physical link, you will need to configure VLAN trunking. This involves designating one or more ports as trunk ports and configuring the trunking protocol, such as IEEE 802.1Q or Cisco’s proprietary ISL protocol.
- Configure VLAN Interfaces: If you need to allow VLAN traffic to be routed between different subnets, you will need to configure VLAN interfaces. This involves assigning an IP address to a VLAN interface and configuring routing protocols as needed.
- Verify Configuration: Once you have configured VLANs, it is essential to verify the configuration to ensure that traffic is being sent and received correctly. This involves checking that ports are correctly assigned to VLANs, that VLAN traffic is being properly tagged, and that VLAN interfaces are correctly configured.
VLAN configuration requires a solid understanding of the underlying technology and best practices for VLAN design and implementation. Network administrators must also ensure that they follow security best practices to prevent unauthorized access to VLANs and maintain the integrity of the network.
VLAN vs. LAN
A VLAN (Virtual Local Area Network) and a LAN (Local Area Network) are both networking technologies used to connect devices in a specific area. However, there are significant differences between the two:
- Scope: A LAN is a physical network that connects devices within a specific geographic location, such as a home, office, or campus. In contrast, a VLAN is a logical network that can span multiple physical LANs, allowing devices to be grouped together based on their function, location, or other criteria.
- Segmentation: LANs typically use physical segmentation, such as separate switches or routers, to separate traffic between different groups of devices. VLANs use logical segmentation, meaning that traffic is separated based on VLAN IDs and VLAN tags that are added to network packets.
- Configuration: LANs are typically configured using physical devices such as switches, routers, and access points. In contrast, VLANs are configured using software, typically through the switch or router’s management interface.
- Scalability: LANs can be limited by the number of physical devices that can be connected to them. VLANs, on the other hand, can support much larger networks by allowing logical segmentation of traffic across multiple physical LANs.
- Security: VLANs can be used to increase network security by isolating traffic between different groups of devices. In contrast, LANs provide limited security as all devices connected to the same physical network can communicate with each other.
VLANs provide greater flexibility, scalability, and security than LANs by allowing logical segmentation of network traffic across multiple physical networks. However, configuring and managing VLANs requires additional knowledge and expertise compared to LANs, making them more complex to set up and maintain.
Future of VLANs
VLANs have been a key technology for network segmentation and isolation for many years, and they will continue to be an important tool for network administrators in the foreseeable future. While there are newer technologies such as Software-Defined Networking (SDN) and Network Function Virtualization (NFV) that can provide similar network segmentation and isolation capabilities, VLANs remain a reliable and widely-used technology for managing network resources.
In the future, VLANs may become even more important as organizations increasingly adopt hybrid cloud and multi-cloud environments. VLANs can help provide network segmentation and isolation in these environments, allowing organizations to maintain security and compliance while also enabling more flexible and scalable network architectures.
There may also be advancements in VLAN technology that improve performance, security, and manageability. For example, new VLAN standards such as Virtual Extensible LAN (VXLAN) and Generic Routing Encapsulation (GRE) can provide more flexible and scalable network architectures, while also improving security by enabling encryption of VLAN traffic.
While newer network technologies such as SDN and NFV are gaining popularity, VLANs will remain a key technology for network segmentation and isolation for many years to come. As organizations continue to adopt more complex network architectures and cloud environments, VLANs will be an important tool for ensuring that network resources are properly managed and secured.
FAQs about VLAN
What is a VLAN?
A VLAN is a logical network segment that groups together a set of devices based on specific criteria, such as physical location, department, or application.
What are the benefits of using VLANs?
The benefits of using VLANs include improved network performance, increased security, simplified network management, and more efficient use of network resources.
How do VLANs work?
VLANs work by assigning a unique identifier or VLAN tag to each network packet, which allows network switches to identify and route traffic between different VLANs.
What is VLAN tagging?
VLAN tagging is a process of adding a VLAN tag or identifier to each network packet to identify the VLAN to which the packet belongs.
What are the different types of VLANs?
The different types of VLANs include port-based VLANs, MAC-based VLANs, protocol-based VLANs, and VLAN trunking.
How do you configure VLANs?
VLANs can be configured through the network switch’s management interface or command-line interface, using tools such as the Cisco IOS VLAN Configuration Guide.
What is VLAN hopping?
VLAN hopping is a security vulnerability that allows an attacker to gain unauthorized access to network resources by exploiting misconfigured VLANs.
How do you troubleshoot VLAN problems?
VLAN problems can be diagnosed using network monitoring tools such as packet sniffers, network analyzers, and switch logs, as well as by checking the configuration of network devices and VLAN tags.
Can VLANs be used in virtualized environments?
Yes, VLANs can be used in virtualized environments to provide network segmentation and isolation for virtual machines, containers, and network functions.
What is the future of VLANs?
VLANs will remain an important technology for network segmentation and isolation for the foreseeable future, as organizations increasingly adopt hybrid cloud and multi-cloud environments, and as advancements in VLAN technology continue to improve performance, security, and manageability.
In conclusion, VLANs are a crucial technology for network segmentation and isolation that provide many benefits to organizations, including improved network performance, increased security, simplified network management, and more efficient use of network resources. There are different types of VLANs, each with its own advantages and considerations.
To implement VLANs in your network, it is essential to follow best practices, diagnose and resolve common problems, and ensure proper configuration and management. Additionally, VLANs can be used in virtualized environments, and their importance will continue to grow as organizations adopt hybrid cloud and multi-cloud architectures.
If you are looking to improve your network performance, security, and management, implementing VLANs is a recommended solution. By following the best practices and recommendations outlined in this guide, you can effectively use VLANs to create logical network segments that improve network performance and security while simplifying network management.

Information Security Asia is the go-to website for the latest cybersecurity and tech news in various sectors. Our expert writers provide insights and analysis that you can trust, so you can stay ahead of the curve and protect your business. Whether you are a small business, an enterprise or even a government agency, we have the latest updates and advice for all aspects of cybersecurity.