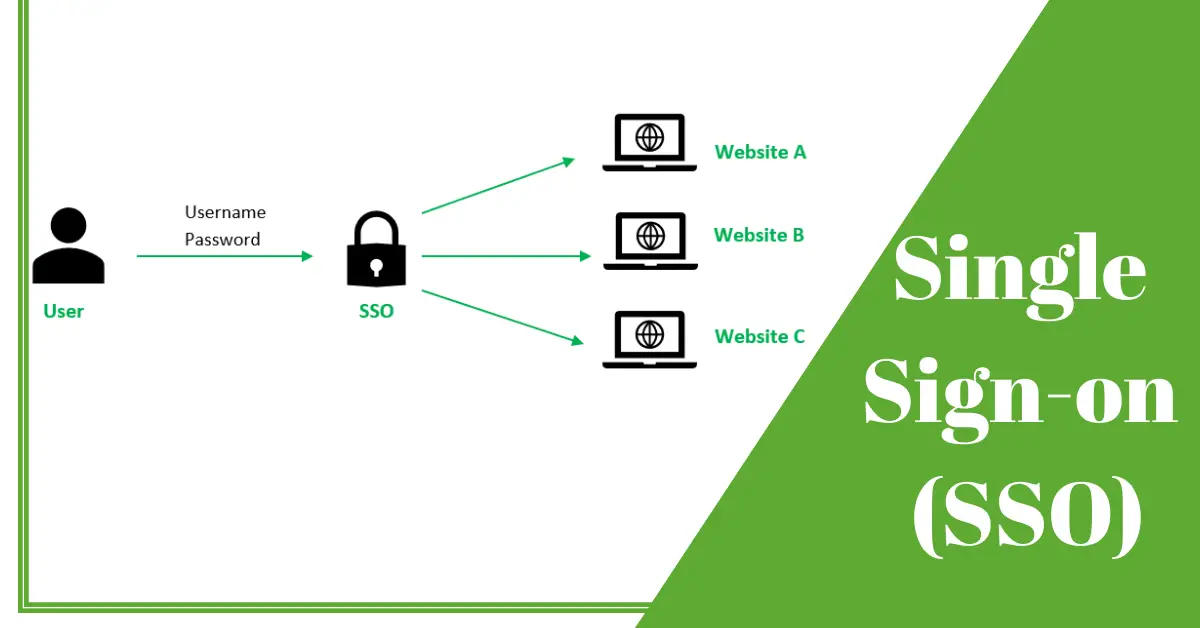
What is Single Sign-on (SSO)? Single sign-on (SSO) enables access to services, applications, or resources via a single authentication process. SSO replaces individual logon procedures with different user data and uses an overarching identity for the user.
Authentication is a fundamental aspect of digital security that plays a pivotal role in safeguarding sensitive information and ensuring the integrity of online interactions. In today’s interconnected world, where virtually every aspect of our lives involves digital technology, the importance of authentication cannot be overstated. This article explores the significance of authentication and provides a glimpse into how Single Sign-On (SSO) simplifies this crucial aspect of digital security.
Contents
- What is Authentication?
- The Challenge of Multiple Logins
- What is Single Sign-On (SSO)?
- How SSO Simplifies Authentication
- How SSO Works
- Role of Identity Providers and Service Providers
- Benefits of SSO
- Types of SSO
- Use Cases and Examples
- Implementing SSO
- Common Challenges and How to Overcome Them
- Security Considerations
- SSO and Regulatory Compliance
- Limitations and Drawbacks of SSO
- Alternatives to SSO
- SSO in a Modern Digital Landscape
- Future Trends and Developments in SSO
- Frequently Asked Questions
What is Authentication?
Authentication, in the context of the digital world, refers to the process of verifying the identity of a user, device, or system attempting to access a particular resource or perform a specific action. It involves confirming that the entity seeking access is indeed who or what it claims to be. In essence, authentication acts as a digital gatekeeper, ensuring that only authorized entities gain entry to protected digital spaces.
The Critical Role of Authentication in Security
Authentication is the first line of defense against unauthorized access, data breaches, identity theft, and a wide range of cyber threats. Several key factors underpin its importance:
- Access Control: Authentication determines who can access what within a system or network. It ensures that only legitimate users can access sensitive data or perform privileged actions, thereby reducing the risk of unauthorized data exposure or malicious activities.
- Data Protection: By verifying the identity of users, authentication helps protect sensitive information from falling into the wrong hands. This is especially critical in industries like healthcare, finance, and e-commerce, where the loss of data can have serious consequences.
- Identity Verification: In an age of digital impersonation and identity theft, robust authentication methods are essential for confirming that users are who they claim to be. This verification process is crucial for online banking, e-commerce transactions, and accessing personal accounts.
- Compliance: Many regulatory standards and data protection laws, such as GDPR and HIPAA, mandate strong authentication measures to safeguard sensitive data. Failure to comply with these regulations can result in severe legal and financial penalties.
- Cybersecurity: Authentication is a cornerstone of cybersecurity. It helps prevent unauthorized access to systems and networks, reducing the likelihood of malware infections, insider threats, and other security breaches.
Single Sign-On (SSO) is a powerful solution that streamlines the authentication process. It allows users to log in once and gain access to multiple applications or services without the need to enter their credentials repeatedly. SSO enhances user convenience while maintaining security.
In the upcoming sections, we’ll delve deeper into how SSO achieves this and why it has become a popular choice for organizations aiming to simplify authentication without compromising on safety.
The Challenge of Multiple Logins
Individuals and organizations often grapple with the cumbersome task of managing multiple login credentials. This challenge arises due to the sheer number of online services, applications, and platforms we use on a daily basis. Here, we’ll explore the problems users encounter with multiple login credentials and the security risks associated with password management.
Problems Users Face with Multiple Login Credentials
- Password Fatigue: Users are bombarded with a multitude of usernames and passwords for various online accounts, making it difficult to remember them all. This leads to “password fatigue,” where users may resort to using weak, easily guessable passwords or reusing the same password across multiple sites.
- Forgetfulness: The human brain can only retain so many complex passwords. As a result, users often forget their login credentials, leading to frustration and the need to reset passwords regularly.
- Time and Effort: Logging in repeatedly to different services consumes time and effort, especially in work environments where employees need access to various tools and applications.
- Security Risks: Managing numerous passwords increases the likelihood of security lapses. Weak passwords and password reuse create vulnerabilities that malicious actors can exploit.
Security Risks Associated with Password Management
- Password Weakness: Users may opt for simple and easily guessable passwords due to the difficulty of remembering complex ones. These weak passwords are susceptible to brute-force attacks and password cracking.
- Password Reuse: When users use the same password across multiple sites, a breach on one platform can compromise their accounts on others. Cybercriminals often target low-security websites to gain access to more critical services.
- Phishing: Users receiving phishing emails may inadvertently divulge their login credentials, especially if they believe the email is from a legitimate source. Phishers exploit this human vulnerability to steal passwords.
- Credential Stuffing: Cybercriminals often obtain lists of stolen usernames and passwords from data breaches. They then attempt to use these credentials to gain unauthorized access to other accounts, knowing that people often reuse passwords.
What is Single Sign-On (SSO)?
Single Sign-On (SSO) is a centralized authentication process allowing users to access multiple applications, services, or platforms with a single login credentials. Instead of remembering numerous usernames and passwords, users only need to authenticate themselves once to gain access to all linked resources.
How SSO Simplifies Authentication
SSO simplifies authentication in several ways:
- Reduced Credential Burden: Users only need to remember one set of login credentials, significantly reducing the number of passwords they must manage.
- Improved User Experience: SSO enhances the user experience by eliminating the need for repetitive logins. This boosts productivity and reduces frustration.
- Enhanced Security: While SSO reduces the number of passwords, it can also improve security. Organizations can enforce stronger authentication methods for the single sign-on process, such as multi-factor authentication (MFA), to bolster security.
- Centralized Management: IT departments can centralize user authentication and access control, making it easier to enforce security policies, track user activity, and respond to security incidents.
- Streamlined Access: Users can seamlessly access various applications and services, both on-premises and in the cloud, with a single sign-on action, promoting efficiency and accessibility.
- Revocation and Monitoring: When an employee leaves an organization or a user’s access needs to be revoked, SSO allows for immediate and comprehensive access control. IT administrators can promptly disable access to all linked resources.
How SSO Works
Single Sign-On (SSO) simplifies the authentication process by allowing users to log in once and gain access to multiple applications or services without the need to enter their credentials repeatedly. The SSO process typically involves the following steps:
- User Authentication: When a user attempts to access an application or service that is part of the SSO system, they are redirected to an SSO login page. Here, they enter their credentials, which could include a username and password, and sometimes an additional authentication factor like a one-time code or biometric data.
- Identity Provider (IDP) Authentication: The entered credentials are sent to the Identity Provider (IDP), which is responsible for authenticating the user. The IDP verifies the user’s identity by checking the credentials against its database or by using an external authentication method, such as an LDAP server or a social media account.
- SSO Token Generation: Once the user is successfully authenticated, the IDP generates a secure token. This token serves as proof of authentication and contains information about the user’s identity, as well as any additional attributes or permissions associated with the user.
- Token Handoff to Service Provider (SP): The user is then redirected back to the application or service they initially wanted to access, but this time, they don’t need to re-enter their credentials. Instead, the token is presented to the Service Provider (SP).
- Service Provider Validation: The SP receives the token and validates it. It checks the token’s signature and may also consult the IDP or a trusted source to ensure the token is genuine and the user’s session is still valid.
- User Access: If the token is valid, the SP grants the user access to the requested application or service without requiring the user to log in again. The user can now interact with the resource seamlessly.
Role of Identity Providers and Service Providers
Identity Provider (IDP): The IDP is the central component of the SSO system. It is responsible for authenticating users and generating the SSO tokens. It stores user identity information, manages access policies, and enforces security measures. Common examples of IDPs include Active Directory, Okta, and Google Identity Platform.
Service Provider (SP): The SP is any application, service, or platform that a user wants to access using SSO. It relies on the IDP to authenticate users. Once the SP receives a valid SSO token, it trusts the token’s authenticity and grants access to the user. Examples of SPs can range from cloud-based applications like Salesforce and Dropbox to in-house services like email servers or custom applications.
Benefits of SSO
Improved User Experience
- Simplified Access: Users enjoy the convenience of a single login for multiple services, reducing the hassle of remembering and entering multiple usernames and passwords.
- Time Savings: SSO significantly reduces login times, enhancing productivity and user satisfaction, particularly in environments with numerous applications.
Enhanced Security through Centralized Authentication
- Stronger Authentication Options: SSO systems often allow organizations to implement robust authentication methods, such as multi-factor authentication (MFA), for the initial login, bolstering security.
- Centralized Management: IT administrators have better control over user access, allowing for more effective enforcement of security policies and quicker responses to potential security incidents or unauthorized access.
- Reduced Risk of Password-related Issues: SSO reduces the risk of password-related vulnerabilities like weak passwords and password reuse since users only need to remember one set of credentials.
- Revocation and Monitoring: In case of a security breach or when a user’s access needs to be revoked, SSO allows for immediate and comprehensive access control, reducing exposure to potential threats.
Types of SSO
Enterprise SSO
- Description: Enterprise SSO, also known as ESSO or Windows Integrated Authentication, is primarily used within an organization’s network to provide seamless access to multiple internal resources. It’s commonly associated with Microsoft technologies.
- How It Works: Users log in once when they access their computer or workstation, and that authentication is leveraged to grant access to various applications and resources within the enterprise network without needing to enter credentials again.
Web-based SSO
- Description: Web-based SSO, also known as Web SSO or Browser SSO, is designed for web applications and services, both on-premises and in the cloud. It allows users to access multiple web-based services with a single set of credentials.
- How It Works: Users authenticate once on a central authentication server (Identity Provider or IDP), and then they can access multiple web applications without re-entering credentials. Popular protocols for Web SSO include SAML (Security Assertion Markup Language) and OpenID Connect.
Federated SSO
- Description: Federated SSO extends the concept of SSO beyond an organization’s boundaries. It enables users from one organization to access resources or services in another organization, such as partner companies or cloud service providers, without creating separate user accounts.
- How It Works: Identity Federation protocols like SAML and OAuth are used to establish trust between different organizations. When a user from one organization accesses a resource in another organization, the user’s credentials are validated by their own IDP, and then a trusted assertion or token is provided to the SP in the other organization, granting access.
Use Cases and Examples
Real-world Scenarios Where SSO is Advantageous
- Enterprise Environments: SSO is ideal for large organizations with numerous internal systems and applications. Employees can seamlessly access tools like email, HR software, and intranet portals without repeatedly logging in, improving efficiency.
- Cloud Services: Many businesses rely on cloud-based applications like Salesforce, Google Workspace, and Microsoft 365. SSO simplifies access to these services while enhancing security.
- Educational Institutions: Schools and universities use SSO to give students and faculty easy access to various online learning platforms, library resources, and administrative tools.
- Healthcare: Healthcare providers use SSO for secure access to electronic health records (EHRs), patient management systems, and other critical healthcare applications.
- Financial Services: Banks and financial institutions use SSO to facilitate secure access to online banking, investment platforms, and customer portals.
Examples of Organizations Using SSO Effectively
- Google: Google employs Web SSO for its suite of services, including Gmail, Google Drive, and Google Workspace. Users log in once and can seamlessly access multiple Google applications without re-entering credentials.
- Microsoft: Microsoft uses SSO extensively within its enterprise ecosystem. Windows Integrated Authentication allows users to access various Microsoft services like Office 365, SharePoint, and Azure with a single login.
- Salesforce: Salesforce, a popular customer relationship management (CRM) platform, offers SSO capabilities to streamline access for its users. Organizations can integrate Salesforce with their identity providers.
- Amazon Web Services (AWS): AWS supports federated SSO, enabling organizations to manage access to their cloud resources securely. They can integrate AWS with their existing identity providers using protocols like SAML.
- Higher Education Institutions: Universities often implement SSO solutions to simplify access to learning management systems, student portals, and library resources. For example, the Shibboleth framework is commonly used in the academic sector for federated SSO.
Implementing SSO
Assessment and Planning
- Identify Objectives: Define the specific goals and objectives of implementing SSO. Understand what systems and applications need to be integrated.
- Inventory Resources: Compile a list of all the applications and services that will be part of the SSO ecosystem.
Select an SSO Solution
- Choose the Right Protocol: Select the SSO protocol that best fits your needs, such as SAML, OAuth, or OpenID Connect.
- Evaluate SSO Providers: Research and select a reputable SSO provider or decide if you’ll develop an in-house solution.
Integration and Configuration
- Configure Identity Provider (IDP): Set up the IDP with user databases, policies, and authentication methods.
- Integrate Service Providers (SPs): Configure SPs to trust the IDP for authentication. This often involves configuring each SP individually.
- User Attribute Mapping: Ensure user attributes are correctly mapped between the IDP and SPs to provide the necessary access and permissions.
Testing
- User Testing: Conduct thorough testing with real users to identify and resolve any issues with the SSO implementation.
- Security Testing: To uncover potential weaknesses, perform security testing, including vulnerability assessments and penetration testing.
Deployment
Gradual Rollout: Implement SSO gradually, starting with a subset of applications and expanding over time. Monitor the rollout to address any issues promptly.
User Training
- Education: Train users on how to use SSO and explain the benefits of the system.
- Support: Offer user support for any login or access issues.
Monitoring and Maintenance
- Continuous Monitoring: Implement continuous monitoring to track user activity, detect anomalies, and ensure the security and performance of the SSO system.
- Regular Updates: Keep SSO components up to date with security patches and updates.
Common Challenges and How to Overcome Them
Integration Complexity
Integrating existing applications with SSO can be complex, especially if they don’t support SSO protocols. Consider using identity bridges or custom connectors to address this challenge.
User Adoption
Users may initially resist the change. Provide clear communication, training, and support to help them adapt.
Security Concerns
SSO introduces a single point of failure, making it critical to implement strong security measures. Implement multi-factor authentication (MFA), robust password policies, and regular security audits.
Legacy Systems
Older or proprietary applications may not support modern SSO protocols. In such cases, consider workarounds like reverse proxies or application gateways.
Partner and External Integration
Federated SSO with external organizations may require negotiation, legal agreements, and trust establishment.
Security Considerations
SSO and Security Risks
- Single Point of Failure: SSO introduces a single point of failure; if the central IDP is compromised, attackers could gain access to all linked services.
- Credential Theft: Stolen credentials can lead to unauthorized access across multiple systems.
- Session Hijacking: SSO tokens can be vulnerable to session hijacking if not properly protected.
Best Practices for Securing SSO Implementations
- Strong Authentication: Enforce strong authentication methods, such as MFA, especially for accessing sensitive applications.
- Secure Token Handling: Protect SSO tokens with strong encryption and ensure they have a limited lifespan.
- Audit and Monitoring: Implement robust auditing and monitoring to detect suspicious activities and potential breaches.
- Access Control: Define and enforce access control policies to limit what users can access based on their roles and responsibilities.
- Regular Security Testing: Conduct regular security assessments, including penetration testing and vulnerability scanning, to identify and remediate weaknesses.
- User Education: Educate users on best practices, such as not sharing their credentials and recognizing phishing attempts.
- Incident Response: Have a well-defined incident response plan in place to address security incidents promptly.
- Patch Management: Keep all SSO components and software up to date with security patches.
- Backup and Recovery: Implement backup and recovery procedures to ensure system availability in case of failures.
- Legal and Compliance: Comply with relevant data protection and privacy regulations when handling user data in the SSO system.
SSO and Regulatory Compliance
Single Sign-On (SSO) can significantly aid organizations in complying with data protection laws and regulations. Here’s how SSO contributes to compliance and its implications for specific regulations:
How SSO Aids in Compliance with Data Protection Laws
- Access Control: SSO enables centralized access control, allowing organizations to enforce strict access policies and permissions. This ensures that only authorized individuals have access to sensitive data, aligning with the principles of data protection.
- Authentication Standards: Many data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), require organizations to implement strong authentication measures. SSO can integrate with multi-factor authentication (MFA) methods, enhancing security and compliance.
- User Accountability: SSO systems maintain audit trails, recording user access to different applications and resources. These logs can be invaluable in demonstrating compliance with data protection laws, which often require organizations to track and report data access and usage.
- Consent Management: Some regulations, like GDPR, mandate obtaining explicit user consent for data processing. SSO systems can integrate consent management mechanisms, ensuring that users provide informed consent before accessing certain resources.
- Data Minimization: Data protection laws emphasize the principle of data minimization—organizations should collect and retain only the data necessary for specific purposes. SSO can facilitate this by granting users access to applications based on their roles and eliminating unnecessary data access.
Specific Regulations and SSO Implications
- GDPR (General Data Protection Regulation): SSO can help in GDPR compliance by centralizing access control, maintaining user consent records, and enabling data subject requests. Organizations must ensure that SSO systems handle personal data in compliance with GDPR requirements.
- HIPAA (Health Insurance Portability and Accountability Act): Healthcare organizations can use SSO to enforce strict access controls and audit trails for electronic health records (EHRs). SSO implementations must adhere to HIPAA’s security and privacy requirements.
- CCPA (California Consumer Privacy Act): SSO can assist with CCPA compliance by managing user consent preferences and providing mechanisms for users to exercise their rights. Organizations must ensure that their SSO systems handle personal data in alignment with CCPA standards.
- FERPA (Family Educational Rights and Privacy Act): Educational institutions can utilize SSO to protect student records and maintain strict access controls, ensuring compliance with FERPA regulations regarding the privacy of educational records.
Limitations and Drawbacks of SSO
While SSO offers numerous benefits, it also has limitations and drawbacks to consider:
- Single Point of Failure: If the central identity provider (IDP) experiences downtime or security breaches, it can disrupt access to multiple services.
- Integration Complexity: Integrating existing applications and legacy systems with SSO can be complex and may require custom connectors or workarounds.
- Dependency on Identity Provider: Organizations become highly dependent on the IDP, making it critical to ensure the IDP is highly available and secure.
- User Resistance: Users may initially resist SSO, especially if they are accustomed to the traditional login process.
Situations Where SSO May Not Be Suitable:
- Small Organizations: Small organizations with a limited number of applications and users may not benefit as much from SSO, and the implementation effort might outweigh the advantages.
- Non-Web Applications: SSO is primarily designed for web-based applications. If an organization heavily relies on non-web applications or proprietary software, SSO may not be as effective.
- Highly Regulated Industries: In industries with extremely strict security and compliance requirements, organizations may have concerns about relying on a third-party SSO provider.
- Complex Legacy Systems: Organizations with complex legacy systems that cannot easily integrate with SSO protocols may find the implementation challenging and costly.
Alternatives to SSO
There are several alternative authentication methods organizations can consider when SSO may not be the best fit or in conjunction with SSO for added security:
Traditional Username and Password
Overview: Continue to use traditional username and password authentication for applications and services. This method is simple and familiar to users.
When to Consider: Consider this approach when SSO integration is not practical, or for applications where SSO is not a suitable option.
Multi-Factor Authentication (MFA):
Overview: MFA requires users to provide two or more forms of authentication, such as a password and a one-time code from a mobile app or hardware token. It adds an extra layer of security to login processes.
When to Consider: Implement MFA in conjunction with SSO to enhance security, especially for sensitive applications and data.
Passwordless Authentication
Overview: Passwordless authentication methods eliminate the need for traditional passwords. They can include biometric authentication (e.g., fingerprint or facial recognition), email-based magic links, or hardware-based tokens.
When to Consider: Use passwordless authentication for improved security and user convenience, reducing reliance on passwords.
Social Login
Overview: Social login allows users to sign in using their existing social media credentials (e.g., Google or Facebook). It simplifies the registration and login processes for users.
When to Consider: Implement social login for customer-facing applications or platforms where user convenience is a priority.
Client Certificates
Overview: Client certificates are digital certificates stored on a user’s device, providing a high level of security. Users present these certificates to authenticate.
When to Consider: Use client certificates for applications or environments that require strong authentication and have the necessary infrastructure for certificate issuance and management.
Adaptive Authentication
Overview: Adaptive authentication assesses user behavior and risk factors to determine the level of authentication required. It can adapt security measures based on context.
When to Consider: Employ adaptive authentication to dynamically adjust authentication requirements based on the perceived risk level of a particular access attempt.
SSO in a Modern Digital Landscape
The Role of SSO in the Era of Remote Work and Cloud Computing:
- Remote Work: SSO is crucial for remote work scenarios where employees need secure access to cloud-based applications and services from various locations. It simplifies access and enhances security in distributed work environments.
- Cloud Computing: With the growing adoption of cloud services, SSO plays a pivotal role in providing seamless access to cloud applications while maintaining strong security controls. It bridges the gap between on-premises and cloud resources.
Future Trends and Developments in SSO
- Zero Trust Architecture (ZTA): SSO will likely play a central role in Zero Trust models, where access is strictly controlled and continuously monitored. SSO’s ability to provide contextual access based on user behavior aligns with ZTA principles.
- Passwordless Authentication: Passwordless authentication methods will continue to gain traction, reducing reliance on passwords and improving security. SSO will integrate with these methods for a more secure user experience.
- AI and Behavioral Analytics: SSO systems will increasingly incorporate AI and behavioral analytics to detect anomalies and potential security threats, enhancing risk-based authentication.
- Mobile and Biometric Authentication: The use of mobile devices and biometric authentication (e.g., facial recognition and fingerprint scanning) will become more prevalent in SSO solutions for enhanced security and user convenience.
- Integration with Identity and Access Management (IAM): SSO will continue to integrate with IAM solutions to provide comprehensive identity management, including user provisioning, deprovisioning, and role-based access control.
- Regulatory Compliance: SSO solutions will evolve to better address compliance requirements, including providing audit logs and tools for managing consent and user data.
Frequently Asked Questions
What is Single Sign-On (SSO)?
Single Sign-On (SSO) is an authentication process that allows users to access multiple applications or services using a single set of login credentials. With SSO, users only need to authenticate themselves once, and then they can seamlessly access various resources without repeatedly entering their usernames and passwords.
Why is authentication important in the digital world?
Authentication is vital in the digital world to verify the identity of users and ensure that only authorized individuals or systems have access to sensitive information and resources. It helps protect against unauthorized access, data breaches, and cyberattacks.
What challenges do users face with multiple login credentials?
Users face several challenges with multiple login credentials, including password fatigue, forgetfulness, the time and effort required for multiple logins, and the security risks associated with weak passwords and password reuse.
How does Single Sign-On (SSO) simplify authentication?
SSO simplifies authentication by allowing users to log in once and gain access to multiple applications or services without the need to enter their credentials repeatedly. It reduces the number of passwords users need to remember and enhances user experience.
Can you explain the process of how SSO works?
In SSO, users authenticate once at a central Identity Provider (IDP), which generates a secure token upon successful authentication. This token is then presented to various Service Providers (SPs) to access resources without re-entering credentials. The IDP verifies the token, and if valid, the user gains access.
In conclusion, Single Sign-On (SSO) is a powerful authentication solution that simplifies user access to multiple applications while enhancing security. It addresses the challenges of managing numerous login credentials, offers various benefits, and plays a pivotal role in modern digital environments.
As businesses continue to embrace remote work and cloud technologies, SSO remains a key component in providing secure and seamless access to resources. Consider exploring SSO solutions to bolster both user convenience and cybersecurity in your organization.

Information Security Asia is the go-to website for the latest cybersecurity and tech news in various sectors. Our expert writers provide insights and analysis that you can trust, so you can stay ahead of the curve and protect your business. Whether you are a small business, an enterprise or even a government agency, we have the latest updates and advice for all aspects of cybersecurity.