In this digital age, the need for encryption has never been more critical.
Contents
- What is Encryption?
- What Is PGP Encryption?
- How PGP Works
- PGP: Key Components
- Benefits of PGP Encryption
- PGP in Practice
- PGP: Common Misconceptions
- Implementing PGP Encryption
- PGP: Challenges and Limitations
- PGP Encryption Best Practices
- Frequently Asked Questions
- What is PGP encryption used for?
- Is PGP encryption considered secure?
- Can I use PGP encryption for mobile communication?
- Are there free PGP encryption tools available?
- How do I know if my PGP key has been compromised?
- Can PGP encryption be used for cloud storage security?
- What is the difference between PGP and SSL/TLS encryption?
- Are there any legal concerns related to PGP encryption?
- Is PGP encryption vulnerable to quantum computing attacks?
- Can PGP be used for encrypting voice calls?
What is Encryption?
Encryption, in its simplest form, is a protective cloak for your digital messages and data. It scrambles information into an unreadable code, ensuring that only the intended recipient can decipher it. This cloak is essential for safeguarding the secrets we share, be it personal messages, financial transactions, or sensitive documents.
Confidentiality and privacy are the keystones of a secure digital world. Imagine the chaos if our bank transactions, medical records, or personal conversations fell into the wrong hands. Encryption acts as a guardian, upholding our right to privacy and shielding our sensitive information from cybercriminals, hackers, and even government surveillance.
Imagine sending a letter to a friend, but instead of using a sealed envelope, you send it in a transparent one for the world to see. Sounds absurd, right?
Yet, every time we share information online or through electronic devices without encryption, we’re essentially doing just that—exposing our private thoughts and data to prying eyes.
In this digital age, the need for encryption has never been more critical.
What Is PGP Encryption?
PGP, or Pretty Good Privacy, is a comprehensive data encryption and decryption program that provides cryptographic privacy and authentication for data communication. It was developed as a pioneering encryption solution by Phil Zimmermann in 1991. Zimmermann initially created PGP to offer individuals and organizations a means to secure their digital communications and data, especially in the face of increasing concerns about privacy and surveillance in the digital age.
Key Features
- Data Encryption: PGP excels in encrypting data, ensuring that only authorized parties with the appropriate decryption key can access the information. This is fundamental for preserving the confidentiality and privacy of sensitive data.
- Digital Signatures: PGP allows users to create digital signatures, which verify the authenticity and integrity of digital messages and documents. Digital signatures ensure that a message has not been tampered with during transmission and that it indeed came from the expected sender.
- Key Management: PGP offers a robust key management system, allowing users to generate, store, and share encryption keys securely. Effective key management is crucial for maintaining the security of encrypted communications.
- Cross-Platform Compatibility: PGP is designed to work on various operating systems and is compatible with numerous email and file transfer protocols, making it versatile for securing communications across different platforms.
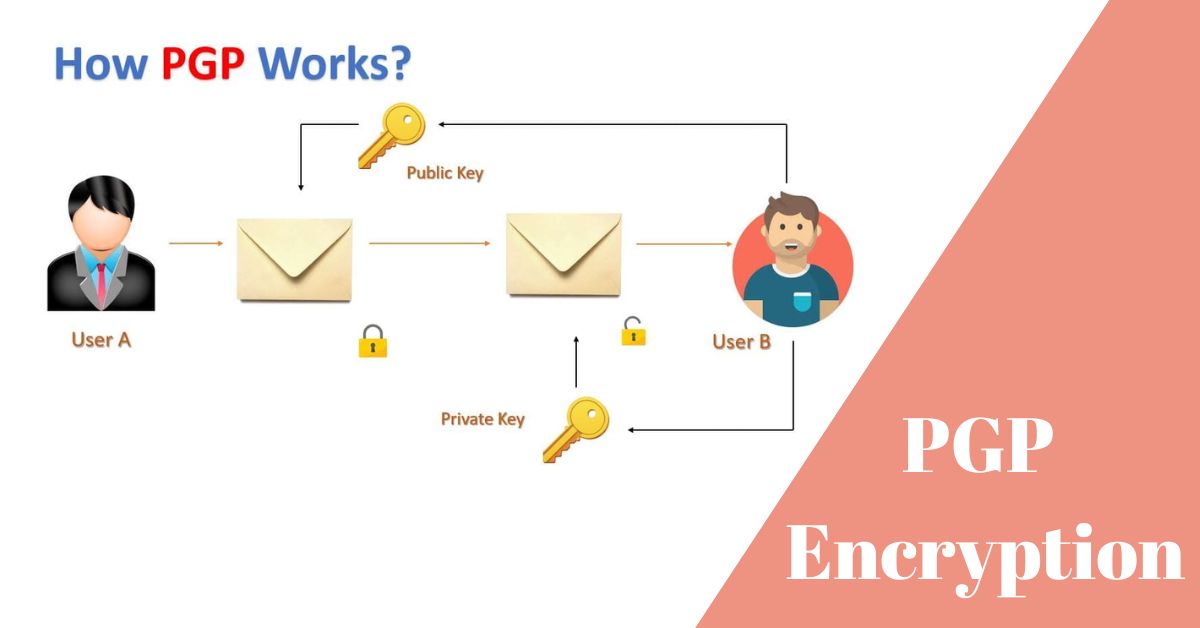
How PGP Works
PGP employs a process known as asymmetric cryptography, which involves the use of two distinct keys: a public key and a private key.
- Encryption Process: When a user wants to send an encrypted message or file to another party, they use the recipient’s public key to encrypt the data. This encrypted data can only be decrypted by the recipient using their corresponding private key.
- Digital Signatures: To ensure the authenticity of a message, the sender can create a digital signature using their private key. The recipient can then verify this signature using the sender’s public key, confirming that the message has not been altered in transit and that it genuinely came from the sender.
PGP: Key Components
PGP comprises several essential components that play critical roles in its functionality:
- Keys: PGP uses a pair of keys for each user—a public key and a private key. The public key is used for encryption and verifying digital signatures, while the private key is kept secret and used for decryption and creating digital signatures.
- Keyrings: Keyrings are files that store public and private keys. A user’s public keyring contains the public keys of other users, while their private keyring stores their private key. Keyrings are essential for key management.
- Key Servers: PGP users can upload their public keys to key servers, making it easier for others to find and use their public keys for encryption or verification. Key servers facilitate the distribution of public keys in a decentralized manner.
Benefits of PGP Encryption
Data Security
One of the primary benefits of PGP encryption is its ability to ensure data remains confidential:
- Confidentiality: PGP employs strong encryption algorithms to protect data from unauthorized access. When data is encrypted using a recipient’s public key, it can only be decrypted with the corresponding private key. This ensures that even if intercepted during transmission or stored on an insecure server, the data remains unreadable to anyone without the proper decryption key.
- Examples of Sensitive Data Protection: PGP is instrumental in safeguarding various types of sensitive data, such as:
- Emails: PGP can be used to encrypt email communications, ensuring that the content of emails is only accessible to the intended recipients, thwarting eavesdroppers.
- Financial Information: PGP encryption can protect financial transactions, including online banking and payment details, shielding them from potential theft or fraud.
- Medical Records: In healthcare, PGP can secure patient records, protecting individuals’ private medical information from unauthorized access.
- Legal Documents: Legal professionals can use PGP to encrypt confidential legal documents and contracts, ensuring the integrity and confidentiality of legal communications.
Authentication
Another key benefit of PGP encryption is its role in verifying the sender’s identity:
- Sender Verification: PGP enables the creation of digital signatures using a user’s private key. When a recipient receives a digitally signed message, they can use the sender’s public key to verify the signature’s authenticity. This process confirms that the message indeed came from the purported sender and has not been altered during transmission.
- Preventing Impersonation and Phishing Attacks: PGP’s authentication features are crucial in preventing impersonation and phishing attacks. Impersonators cannot generate a valid digital signature without access to the sender’s private key, making it difficult for malicious actors to deceive recipients by pretending to be someone they are not. This helps users trust the authenticity of digital communications.
Non-Repudiation
Non-repudiation is another significant benefit of PGP encryption, particularly in legal and business contexts:
- Explaining Non-Repudiation: Non-repudiation means that a sender cannot deny sending a message or file. When a sender digitally signs a document or message using their private key, they cannot later deny authorship. This feature holds legal weight and can be crucial in situations where proof of communication or agreement is required.
- Use Cases in Legal and Business Contexts: Non-repudiation is essential in legal and business transactions. For example:
- Digital Contracts: In business, PGP-signed digital contracts have legal validity because they provide evidence of the parties’ intent and cannot be easily repudiated.
- Email Correspondence: PGP-signed emails in a professional context can serve as evidence of communication between parties and are admissible in legal disputes.
- Financial Transactions: Non-repudiation is vital in financial transactions, ensuring that parties involved cannot later deny their involvement or authorization for a transaction.
PGP in Practice
Email Encryption
When individuals or organizations want to send confidential emails, they can use PGP to encrypt the message content. The sender typically obtains the recipient’s public key and uses it to encrypt the email. Only the recipient, with access to their private key, can decrypt and read the message.
Advantages for Individuals
- Privacy: For individuals, PGP ensures that personal and sensitive information shared via email remains private, preventing unauthorized access or interception.
- Protection from Eavesdropping: It guards against eavesdroppers, including hackers and government surveillance, ensuring that the content of emails remains confidential.
- Authentication: PGP’s digital signatures help individuals verify the authenticity of emails, ensuring that messages are from legitimate sources.
Advantages for Organizations
- Data Protection: PGP helps organizations protect sensitive information, such as customer data, financial reports, and proprietary information, when shared via email.
- Compliance: In industries with strict regulatory requirements (e.g., healthcare or finance), using PGP for email encryption can help organizations meet compliance standards like HIPAA or GDPR.
- Secure Communication: It facilitates secure communication between employees, clients, and partners, reducing the risk of data breaches or leaks.
File Encryption
Users can employ PGP software to encrypt files or folders before sharing or storing them. This ensures that even if unauthorized individuals access the files, they cannot be opened without the correct decryption key.
Protecting Sensitive Documents
- Legal Documents: Law firms can use PGP to encrypt legal contracts, ensuring the confidentiality of client-attorney communications.
- Financial Reports: Companies can encrypt financial reports and sensitive financial data, safeguarding this critical information from unauthorized access.
- Intellectual Property: PGP can protect intellectual property, research data, and product development plans from theft or corporate espionage.
Secure Communication
PGP’s application extends beyond email and file encryption; it can also secure instant messaging and chat applications:
Role in Securing Instant Messaging
- Encryption of Chat Content: PGP can encrypt the content of instant messages and chat conversations, ensuring that only authorized users can decipher the messages.
- Authentication: Users can use PGP to digitally sign their messages, providing assurance of the sender’s identity.
Ensuring Private Conversations:
- Business Communication: PGP-secured instant messaging is valuable in business settings, where confidentiality and authentication are critical. It ensures that sensitive discussions and data remain private.
- Personal Privacy: On a personal level, individuals can use PGP for secure, private conversations, protecting their personal information from surveillance and unauthorized access.
PGP: Common Misconceptions
1. PGP Is Too Complex
- Addressing the Perception: While PGP encryption might seem daunting, it’s important to dispel the notion that it’s overly complex. Many user-friendly tools and interfaces have been developed to simplify the PGP process, making it accessible even for those without technical expertise.
- Highlighting User-Friendly Tools: Encourage users to explore PGP software with intuitive interfaces. Tools like “Gpg4win” for Windows, “GPG Suite” for macOS, and browser extensions like “Mailvelope” offer simplified PGP encryption for email communication. These tools often provide step-by-step wizards to guide users through the process.
2. PGP Is Only for Tech Experts
- Dispelling the Myth: PGP encryption is not exclusive to IT professionals. It is designed to be accessible to a wider audience, including individuals and organizations concerned about digital privacy. The key is to demystify the technology and provide clear, user-friendly instructions.
- Emphasizing Accessibility: PGP can be utilized by anyone who values digital privacy. It’s essential to promote the idea that anyone with basic computer skills can use PGP by following straightforward instructions and guides.
Implementing PGP Encryption
Installing PGP Software
- Step-by-Step Guide: To simplify the process, provide a step-by-step guide for installing PGP software tailored to the user’s operating system (e.g., Windows, macOS, Linux). Include download links to reputable PGP software.
- Recommendations for Reliable PGP Tools: Suggest well-established PGP software that is widely trusted in the cybersecurity community. Mention options like GnuPG (GPG), Kleopatra, and GPG Suite for macOS.
Generating Keys
- Creating PGP Keys: Walk users through the process of generating PGP keys using their chosen software. This includes selecting key types (RSA, ECC, etc.), key lengths, and creating a strong passphrase.
- Best Practices for Key Management: Emphasize the importance of securely storing private keys, which should never be shared. Encourage users to back up their keys in a secure location, such as a hardware security module (HSM) or encrypted USB drive. Remind them to periodically update their keys for added security.
- User-Friendly Key Management Tools: Mention user-friendly key management tools integrated into some PGP software, such as keyring management in Gpg4win, to make key handling more convenient.
PGP: Challenges and Limitations
Key Management
- Complexities of Managing PGP Keys: Managing PGP keys can be challenging, especially for users with multiple keys for different purposes (e.g., email, files). Users may struggle with key revocation, expiration dates, and understanding when and how to use different keys.
- Addressing Key Loss and Recovery: Losing access to a private key can be a significant problem. Users need to understand the importance of securely backing up their private keys and should have strategies in place for key recovery if they ever lose access to their keys.
Compatibility Issues
- Potential Compatibility Issues: PGP encryption may face compatibility issues with certain email clients and systems. Some email clients may not support PGP natively, requiring users to install plugins or use external software for encryption and decryption.
- Workarounds and Solutions: To address compatibility issues, users can explore workarounds like using webmail clients that support PGP (e.g., ProtonMail), employing browser-based encryption extensions, or using email clients specifically designed for PGP, such as Thunderbird with the Enigmail extension.
Trust and Key Verification
Importance of Verifying PGP Keys: Trust is crucial in PGP encryption. Users need to verify the authenticity of the public keys they receive to prevent malicious actors from intercepting communications and replacing keys.
- Key Signing Parties: Encourage users to participate in key signing parties, where individuals physically meet to verify each other’s identities and exchange public key fingerprints.
- Web of Trust: Explain the concept of a web of trust, where users vouch for the authenticity of others’ keys. This system builds trust over time as more people verify keys.
- Keybase.io: Mention services like Keybase.io, which provide a platform for users to link their online identities (e.g., social media profiles) to their PGP keys, enhancing trust.
PGP Encryption Best Practices
1. Regularly Update Software
Stress the critical importance of keeping PGP software up to date. Developers frequently release updates to address vulnerabilities and enhance security. Users should install these updates promptly to ensure their encryption tools are effective against emerging threats.
2. Secure Key Storage
Recommendations for Safeguarding PGP Keys:
- Use Strong Passphrases: Encourage users to create strong, unique passphrases for their private keys. These passphrases should be difficult to guess and include a combination of letters, numbers, and special characters.
- Back Up Keys Securely: Instruct users to securely back up their private keys in multiple locations. This could include external encrypted storage devices, offline paper backups stored in a safe place, or hardware security modules (HSMs) for added protection.
- Protect Passphrases: Remind users never to share their passphrases, store them in easily accessible locations, or use easily guessable phrases (e.g., “password123”). The security of their private keys depends on the strength of their passphrases.
3. Verify Recipients
- Ensuring Correct Recipients: Stress the importance of verifying the recipient’s identity before sending encrypted data. Users should verify that they are encrypting and sending information to the intended party by cross-referencing key fingerprints or using secure communication channels to exchange keys.
- Double-Check Recipient Information: Encourage users to double-check recipient email addresses or user IDs to prevent sending sensitive information to the wrong person accidentally.
Frequently Asked Questions
What is PGP encryption used for?
PGP encryption is used to secure digital communications and data. It is commonly employed for encrypting emails, files, and messages to protect their confidentiality and integrity from unauthorized access or tampering.
Is PGP encryption considered secure?
PGP encryption is generally considered secure when implemented correctly. However, its security depends on factors like key management, passphrase strength, and the quality of encryption algorithms used. Regularly updating PGP software is also crucial to address potential vulnerabilities.
Can I use PGP encryption for mobile communication?
Yes, you can use PGP encryption for mobile communication. There are PGP-compatible mobile apps and email clients available for various platforms that allow you to encrypt and decrypt messages on mobile devices.
Are there free PGP encryption tools available?
Yes, there are free and open-source PGP encryption tools available, such as GnuPG (GPG), Kleopatra, and GPG Suite for macOS. These tools provide robust encryption capabilities without the need for a paid license.
How do I know if my PGP key has been compromised?
Signs of a compromised PGP key include unexpected changes in key properties, unauthorized access to your encrypted data, or unusual activity associated with your key. Regularly reviewing the status of your key and monitoring for any suspicious activity is advisable.
Can PGP encryption be used for cloud storage security?
PGP encryption can be used to secure files before uploading them to cloud storage services. This adds an extra layer of security by ensuring that even if the cloud storage provider experiences a breach, the encrypted files remain unreadable without the decryption key.
What is the difference between PGP and SSL/TLS encryption?
PGP (Pretty Good Privacy) is primarily used for securing data at rest (e.g., emails and files), while SSL/TLS (Secure Sockets Layer/Transport Layer Security) is used for securing data in transit, such as web traffic between a browser and a web server.
The legality of using PGP encryption varies by jurisdiction. Some countries have regulations governing the use of encryption, while others may have restrictions on strong encryption. It’s essential to be aware of local laws and compliance requirements.
Is PGP encryption vulnerable to quantum computing attacks?
PGP encryption, like many current encryption methods, could be vulnerable to attacks by quantum computers with sufficient processing power. To address this, post-quantum encryption algorithms are being developed to ensure the long-term security of encrypted data.
Can PGP be used for encrypting voice calls?
PGP is primarily designed for text-based encryption, and its use for encrypting voice calls is not common. There are other encryption technologies and apps (e.g., Signal) specifically designed for securing voice calls and video chats.
In an era marked by digital communication and the growing importance of data privacy, PGP encryption emerges as a powerful tool to safeguard sensitive information. It serves as a robust defense against unauthorized access, ensuring that your emails, files, and messages remain confidential and secure.
Though initially perceived as complex, PGP encryption has become more accessible, with user-friendly interfaces and comprehensive guides available.
By following best practices such as regularly updating software, securing PGP keys, and verifying recipients, users can maximize the effectiveness of PGP encryption. It is essential to address common misconceptions, making it clear that PGP is not exclusive to tech experts and is indeed accessible to a broader audience.

Information Security Asia is the go-to website for the latest cybersecurity and tech news in various sectors. Our expert writers provide insights and analysis that you can trust, so you can stay ahead of the curve and protect your business. Whether you are a small business, an enterprise or even a government agency, we have the latest updates and advice for all aspects of cybersecurity.