What is a blue team? A Blue Team has the task of protecting an organization’s IT infrastructure from real attackers as well as from simulated attacks by a Red Team. It is made up of IT security experts from within the organization and differs from standard security teams in that it is constantly alert and ready to defend against attacks and intervenes immediately in the event of security incidents.
Contents
- What is a Blue Team in Cyber Security?
- Blue Team vs. Red Team
- Key Responsibilities of the Blue Team
- Blue Team Tools and Technologies
- Building a Strong Blue Team
- Blue Team Best Practices
- The Evolving Landscape of Blue Teaming
- Real-World Examples of Blue Team Success
- Collaborating with the Red Team
- The Continuous Cycle of Improvement
What is a Blue Team in Cyber Security?
The blue team in cybersecurity refers to the group responsible for defending and protecting an organization’s information systems, networks, and data from cyber threats. Blue team members work to maintain the security and integrity of an organization’s digital assets, ensuring that they are well-prepared to prevent, detect, and respond to security incidents.
Blue Team vs. Red Team
Blue teams and red teams are both integral components of a cybersecurity strategy. While the blue team focuses on defense, the red team simulates cyberattacks to test the effectiveness of an organization’s security measures. Red teams attempt to breach defenses and identify vulnerabilities, while blue teams work to prevent, detect, and respond to these simulated or real-world attacks.
Blue teaming plays a crucial role in maintaining a strong cybersecurity posture for an organization.
- Early Threat Detection: Blue teams use monitoring tools and techniques to identify potential threats and vulnerabilities before they can be exploited by malicious actors.
- Incident Response: Blue teams are responsible for efficiently responding to security incidents when they occur, minimizing the impact and preventing further compromise.
- Vulnerability Management: Blue teams assess and manage vulnerabilities within an organization’s systems and networks, applying patches and updates to minimize risk.
- Policy Enforcement: Blue teams ensure that security policies and best practices are implemented across the organization, helping to maintain compliance with industry regulations and standards.
Key Responsibilities of the Blue Team
Threat Detection and Incident Response
Blue teams use various tools and techniques to monitor network traffic, log data, and system behavior to identify potential security incidents. When an incident occurs, the blue team investigates, mitigates, and coordinates the response to minimize damage and restore normal operations.
Security Monitoring and Analysis
Blue teams continuously monitor network and system activities for signs of unauthorized access, anomalies, and suspicious behavior. They analyze these patterns to identify potential security threats and take appropriate action.
Vulnerability Management
Blue teams regularly assess the organization’s systems and applications for vulnerabilities. They prioritize and remediate these vulnerabilities by applying patches, updates, and security measures to prevent exploitation.
Security Policy Enforcement
Blue teams ensure that the organization’s security policies, procedures, and best practices are followed by all employees. They provide guidance on secure practices and may conduct security awareness training to educate staff about potential risks.
Blue Team Tools and Technologies
Security Information and Event Management (SIEM) Systems
SIEM systems collect, correlate, and analyze log and event data from various sources across an organization’s network and systems. They help blue teams detect and respond to security incidents by providing real-time monitoring and threat detection capabilities.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
IDS and IPS are network security tools that monitor network traffic for suspicious or malicious activities. IDS detects potential threats, while IPS takes action to prevent or block those threats in real-time.
Endpoint Security Solutions
Endpoint security solutions protect individual devices (endpoints) such as computers, laptops, and mobile devices. These tools help prevent malware infections, detect unusual behavior, and enforce security policies on endpoints.
Threat Intelligence Platforms
Threat intelligence platforms gather and analyze information about current and emerging cyber threats. Blue teams use this information to enhance their understanding of potential risks and adjust their security measures accordingly.
Building a Strong Blue Team
Essential Skills and Qualities of Blue Team Members
- Technical Proficiency: Blue team members should have a deep understanding of cybersecurity principles, networking, and various security technologies.
- Problem-Solving: The ability to analyze complex security issues, identify root causes, and develop effective solutions is crucial.
- Attention to Detail: Blue team members need to be meticulous in detecting anomalies and potential threats within vast amounts of data.
- Continuous Learning: The cybersecurity landscape is constantly evolving, so a willingness to learn and adapt to new technologies and threats is essential.
- Critical Thinking: Blue team members must be able to think critically and make quick decisions during security incidents.
- Persistence: Dealing with persistent threats requires determination and persistence in investigating and mitigating risks.
Collaboration and Communication within the Blue Team
Effective communication and collaboration are essential for a successful blue team. Team members must be able to share information, insights, and findings openly. They should work cohesively to respond to incidents and share knowledge to improve the overall security posture.
Training and Continuous Skill Development
Cybersecurity is a rapidly evolving field. Blue team members should receive regular training to stay updated on the latest threats, tools, and techniques. Continuous skill development ensures that the team remains effective in defending against new and emerging threats.
Find Your Preferred Courses on Coursera HERE!
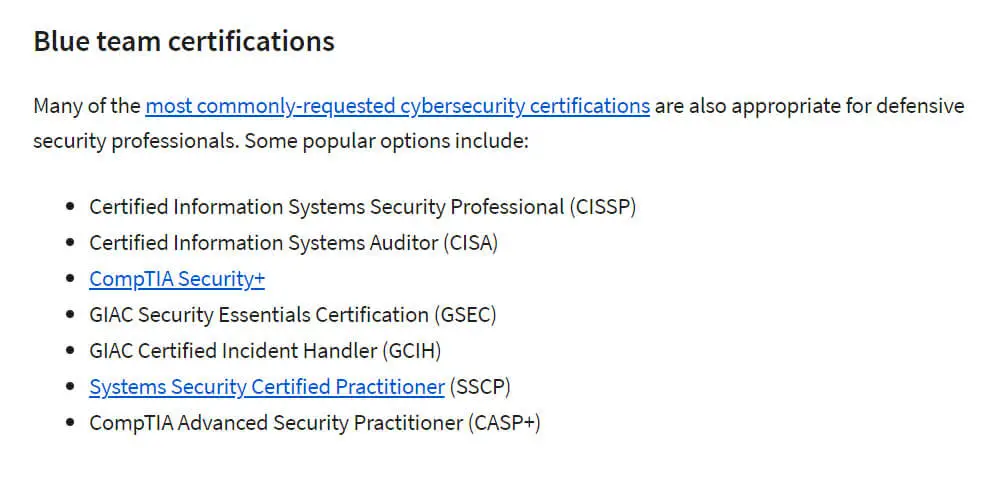
Blue Team Best Practices
Proactive Defense Strategies
Instead of waiting for incidents to occur, blue teams should adopt proactive defense measures. This involves continuous monitoring, threat hunting, and implementing security controls to detect and prevent potential threats before they lead to a breach.
Incident Response Planning and Execution
Develop a well-defined incident response plan that outlines roles, responsibilities, communication procedures, and steps to take in the event of a security incident. Regularly test and refine this plan through tabletop exercises and simulated incident scenarios.
Threat Hunting Techniques
Actively search for signs of undetected threats within your network. This involves analyzing historical data, logs, and network traffic patterns to identify anomalies that may indicate a potential breach.
Regular Security Assessments and Penetration Testing
Conduct regular security assessments and penetration tests to identify vulnerabilities and weaknesses in your systems. This helps you understand how attackers might exploit these vulnerabilities and take corrective actions before a real attack occurs.
The Evolving Landscape of Blue Teaming
Adapting to New Threats and Attack Vectors
Blue teams must stay updated on evolving cyber threats and attack techniques. As attackers develop new tactics, techniques, and procedures, blue teams need to adapt their defense strategies to effectively counter these threats.
Role of Artificial Intelligence and Machine Learning in Blue Teaming
AI and machine learning can enhance blue team capabilities by automating threat detection, analyzing large volumes of data, and identifying patterns that may indicate malicious activities. These technologies can help blue teams respond more quickly and effectively to threats.
Future Trends in Blue Team Methodologies
Blue team methodologies are likely to evolve in response to changing technology and threat landscapes. Some future trends may include more integration of automation and orchestration, increased emphasis on zero-trust architecture, and improved collaboration between blue and red teams.
Real-World Examples of Blue Team Success
Case Study: Targeted Malware Mitigation
In this scenario, a blue team successfully detected and mitigated a sophisticated malware campaign targeting a financial institution. Through continuous monitoring and threat hunting, the blue team identified the malware’s presence, contained its spread, and removed it from the network before it could lead to data exfiltration or financial losses.
Case Study: Responding to a Data Breach
In the aftermath of a data breach, a blue team effectively managed the incident response process. They isolated compromised systems, initiated forensic analysis to determine the extent of the breach, communicated with stakeholders transparently, and implemented security enhancements to prevent similar incidents in the future.
Lessons Learned from High-Profile Incidents
Blue teams often study and learn from high-profile incidents, such as the Equifax breach or the SolarWinds supply chain attack. By analyzing the attack methods, tactics, and vulnerabilities exploited in these incidents, blue teams can improve their defense strategies and better prepare for similar threats.
Collaborating with the Red Team
Blue vs. Red: Working in Harmony
Blue and red teams have complementary roles: blue teams defend, while red teams simulate attacks. These teams can collaborate to strengthen an organization’s overall security posture by sharing insights, tactics, and lessons learned from simulated scenarios.
Benefits of Red and Blue Team Collaboration
Collaboration between red and blue teams helps identify vulnerabilities, improve incident response capabilities, and validate the effectiveness of security measures. Red team assessments provide realistic insights into potential attack vectors, which the blue team can then address and defend against.
Conducting Joint Exercises and Simulations
Regular joint exercises, such as red team vs. blue team simulations, help both teams refine their skills and improve their coordination. These exercises replicate real-world attack scenarios and allow the blue team to practice detecting, responding to, and mitigating threats effectively.
The Continuous Cycle of Improvement
Learning from Mistakes and Failures
Blue teams learn from their mistakes and failures, using post-incident analysis to identify what went wrong and how to prevent similar incidents in the future. This analysis contributes to enhancing defense strategies and incident response procedures.
Incorporating Feedback for Enhancements
Feedback from red team assessments, incident response exercises, and continuous monitoring helps blue teams identify areas for improvement. This feedback loop ensures that the blue team’s defenses evolve to counter new and evolving threats.
Adapting Strategies Based on Emerging Threats
Blue teams stay vigilant and proactive by continuously monitoring the threat landscape. They adapt their strategies and security measures to address emerging threats, leveraging threat intelligence and industry best practices.
In cybersecurity, the blue team stands as the stalwart defender, tirelessly safeguarding organizations from the relentless onslaught of cyber threats. Through proactive strategies, real-world case studies, and seamless collaboration with the red team, they fortify digital fortresses and learn from their experiences.
Find Your Preferred Courses on Coursera HERE!
Embracing a continuous cycle of improvement, blue teams evolve alongside emerging threats, weaving a tapestry of resilience. As technology advances, their dedication to vigilance, adaptation, and relentless pursuit of excellence ensures that the digital realm remains secure. The blue team’s success is not just a victory for the defenders but a safeguard for the entire digital realm.

Information Security Asia is the go-to website for the latest cybersecurity and tech news in various sectors. Our expert writers provide insights and analysis that you can trust, so you can stay ahead of the curve and protect your business. Whether you are a small business, an enterprise or even a government agency, we have the latest updates and advice for all aspects of cybersecurity.

