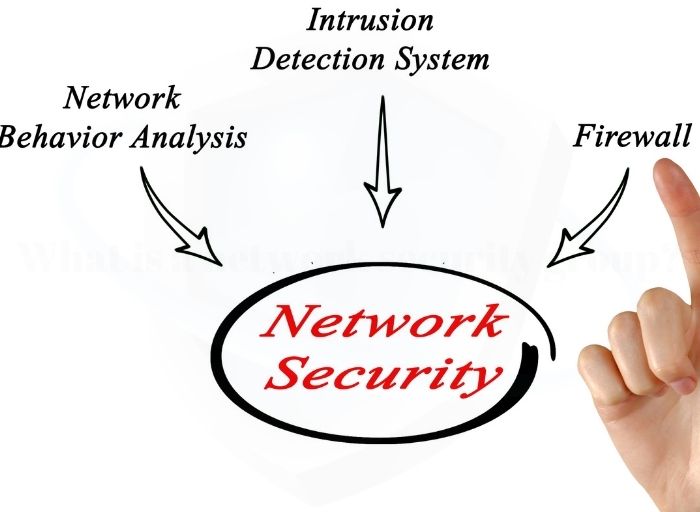
What is a PSK (Pre-shared Key)?
A pre-shared key is a key that is used for symmetric encryption methods. In order to encrypt and decrypt data, the pre-shared keys must first be exchanged between the participants involved. Whoever is in possession of the pre-shared key can use the same key to encrypt and decrypt data. Are you tired of your neighbors … Read more